Deep Analysis of Phobos Ransomware
sample SHA256: a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2
Initial Analysis
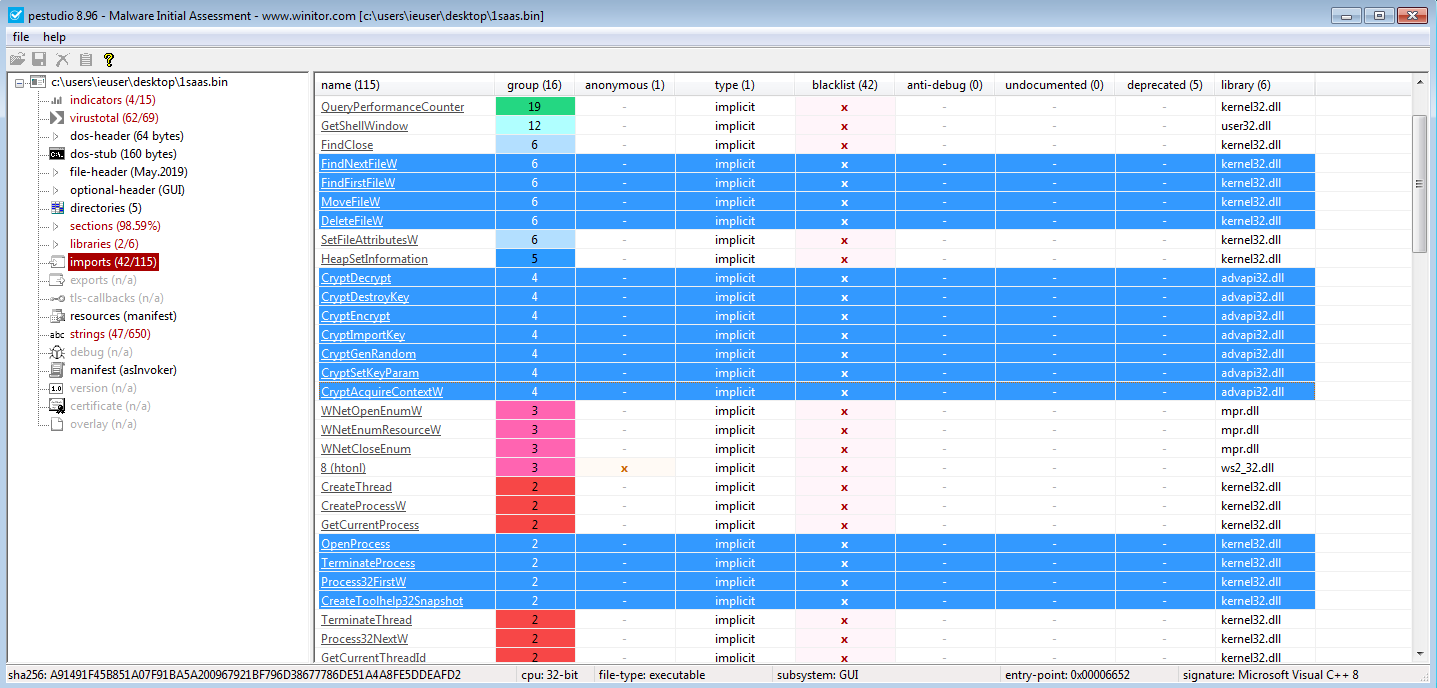
First I loaded the binary into pestudio.
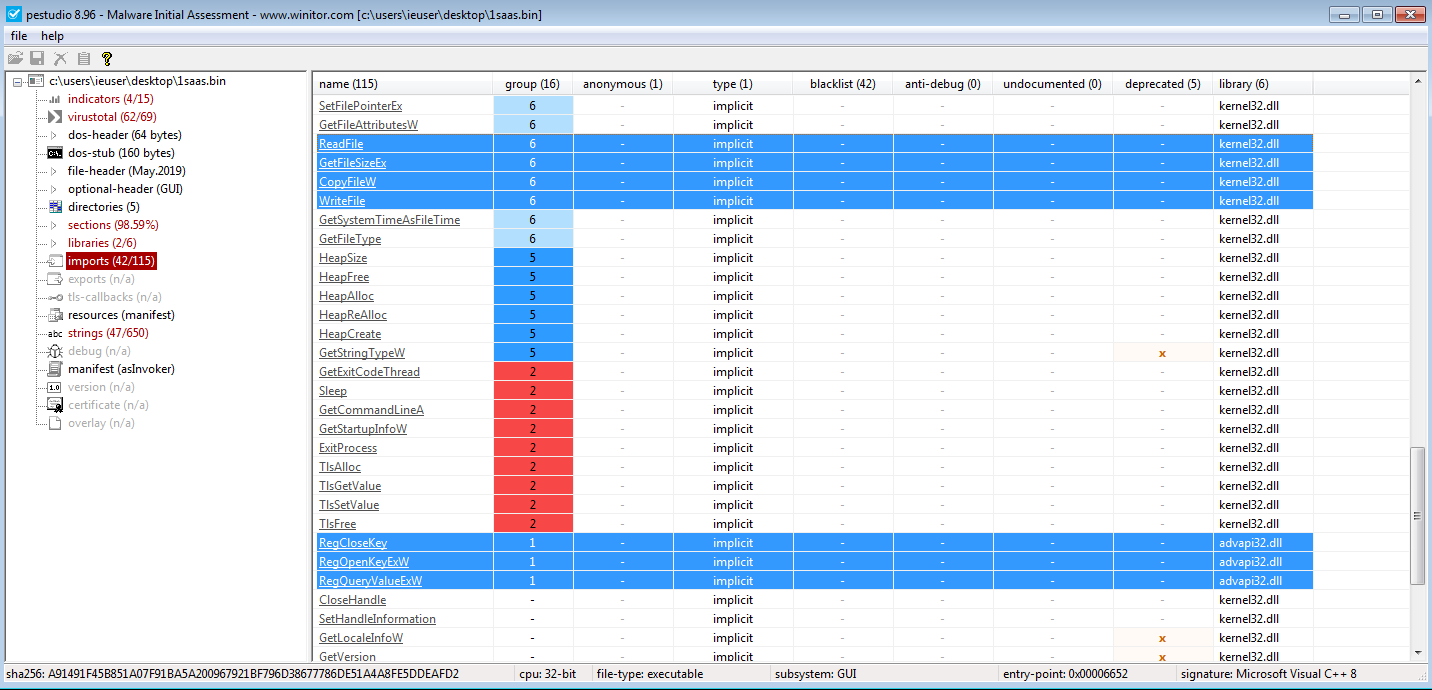
We can see some interesting imports with different functionalities like: file traversal, crypto stuff, file read&write, processes traversal, …
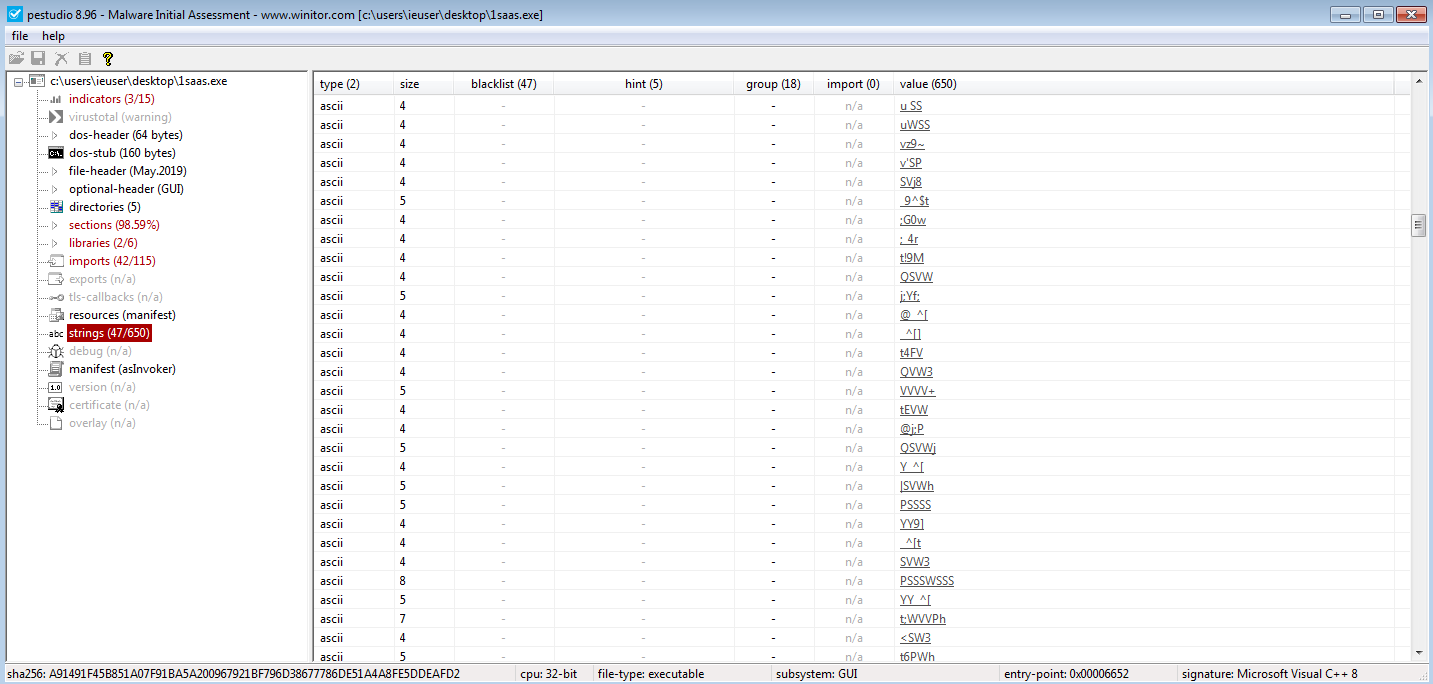
There is not much readable strings here which might indicate the strings are somewhat obfuscated.
Behavioral analysis
If we run ransomware we can see that it asks for administrator privileges.
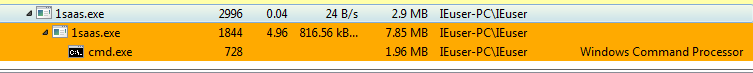
If we accept it and use ProcessHacker we can see that it spawns another copy of itself with the elevated privileges.
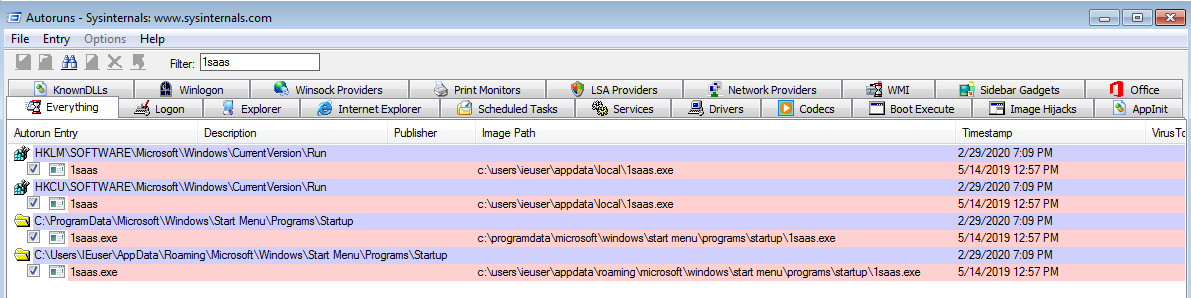
Using Autoruns from sysinternals we can see that it adds a value to the registry and copies itself to the startup folder to maintain persistence, which means that it can encrypt new files.
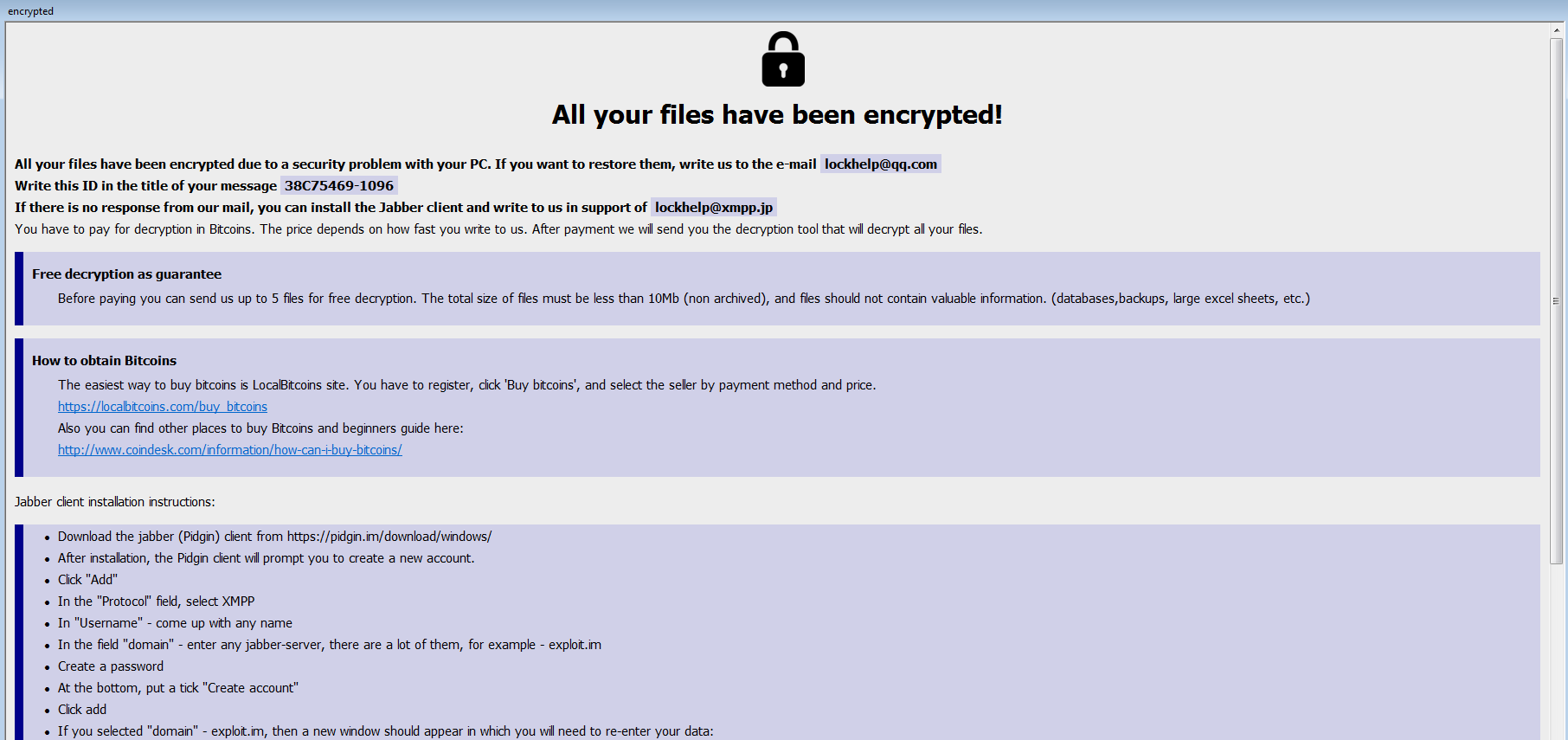
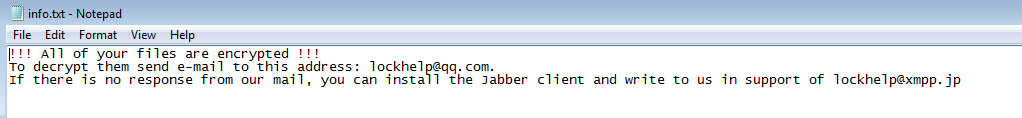
If we let the ransomware run for while we can see it drops its note in two formats: .hta & .txt
The encrypted files are renamed to <Original Name>.id[<Victim ID>].[lockhelp@qq.com].<Ransomware extension>
Going Deep
Now Let’s fire up IDA and see how it goes.
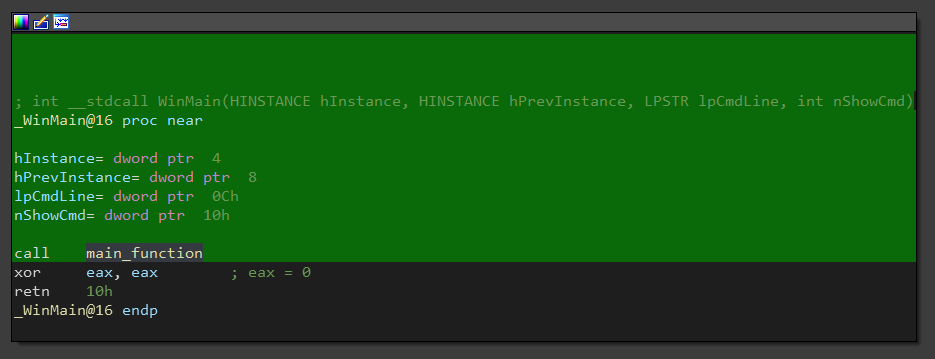
The winMain function just calls main_function.
main_function creates a bunch of threads for different tasks like traversing and encrypting files, killing blacklisted processes and so on.
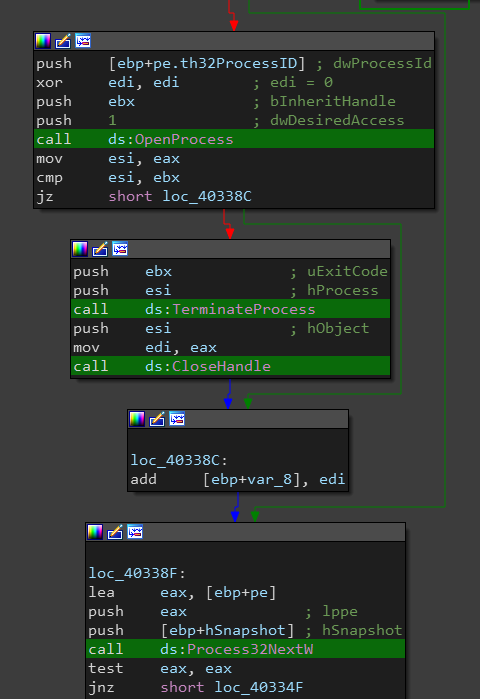
Killing Blacklisted Processes
The ransomware loops through running processes to search and kill blacklisted ones at sub_4032FA
 |
 |
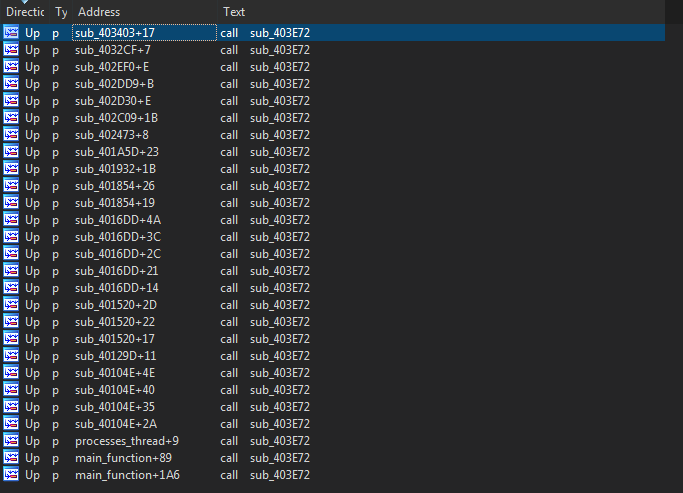
The blacklisted processes are passed to this function as an argument, we can go a step back using Xrefs to know what the blacklisted processes are.
The caller function calls sub_403E72 first, using a debugger we can see the list of the processes returned.
Here is the complete list:
msftesql.exe sqlagent.exe sqlbrowser.exe sqlservr.exe sqlwriter.exe oracle.exe ocssd.exe dbsnmp.exe
synctime.exe agntsvc.exe mydesktopqos.exe isqlplussvc.exe xfssvccon.exe mydesktopservice.exe
ocautoupds.exe agntsvc.exe agntsvc.exe agntsvc.exe encsvc.exe firefoxconfig.exe tbirdconfig.exe
ocomm.exe mysqld.exe mysqld-nt.exe mysqld-opt.exe dbeng50.exe sqbcoreservice.exe excel.exe
infopath.exe msaccess.exe mspub.exe onenote.exe outlook.exe powerpnt.exe steam.exe thebat.exe
thebat64.exe thunderbird.exe visio.exe winword.exe wordpad.exe
Decrypting Strings
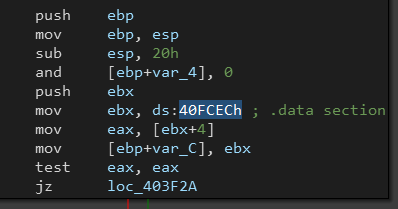
Going back to sub_403E72 (which returned the blacklisted processes), we can see that it’s called multiple times across the code.
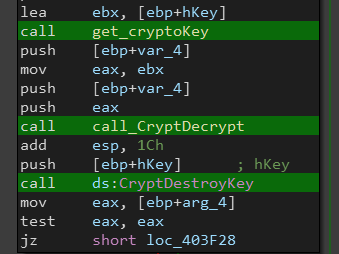
If we look inside it we can see that it loads some data from the .data section then gets a cryptographic key and calls CryptDecrypt. This indicated that the .data section is encrypted and the code uses this function to decrypt data on demand (not decrypted all at once), this also explains why we didn’t find readable strings in the initial analysis.
 |
 |
What is attacked
After calling the decryption function multiple times we can see some interesting strings in the .data section:
-
Ransomware possible extensions:
.acute .actin .acton .actor .acuff .acuna .acute .adage .adair .adame .banhu .banjo .banks .banta .barak .caleb .cales .caley .calix .calle .calum .calvo .deuce .dever .devil .devoe .devon .devos .dewar .eight .eject .eking .elbie .elbow .elder .phobos .help .blend .bqux .com .mamba .karlos .ddos .phoenix .plut .karma .bbc .capital -
Attacked extensions:
.1cd .3ds .3fr .3g2 .3gp .7z .accda .accdb .accdc .accde .accdt .accdw .adb .adp .ai .ai3 .ai4 .ai5 .ai6 .ai7 .ai8 .anim .arw .as .asa .asc .ascx .asm .asmx .asp .aspx .asr .asx .avi .avs .backup .bak .bay .bd .bin .bmp .bz2 .c .cdr .cer .cf .cfc .cfm .cfml .cfu .chm .cin .class .clx .config .cpp .cr2 .crt .crw .cs .css .csv .cub .dae .dat .db .dbf .dbx .dc3 .dcm .dcr .der .dib .dic .dif .divx .djvu .dng .doc .docm .docx .dot .dotm .dotx .dpx .dqy .dsn .dt .dtd .dwg .dwt .dx .dxf .edml .efd .elf .emf .emz .epf .eps .epsf .epsp .erf .exr .f4v .fido .flm .flv .frm .fxg .geo .gif .grs .gz .h .hdr .hpp .hta .htc .htm .html .icb .ics .iff .inc .indd .ini .iqy .j2c .j2k .java .jp2 .jpc .jpe .jpeg .jpf .jpg .jpx .js .jsf .json .jsp .kdc .kmz .kwm .lasso .lbi .lgf .lgp .log .m1v .m4a .m4v .max .md .mda .mdb .mde .mdf .mdw .mef .mft .mfw .mht .mhtml .mka .mkidx .mkv .mos .mov .mp3 .mp4 .mpeg .mpg .mpv .mrw .msg .mxl .myd .myi .nef .nrw .obj .odb .odc .odm .odp .ods .oft .one .onepkg .onetoc2 .opt .oqy .orf .p12 .p7b .p7c .pam .pbm .pct .pcx .pdd .pdf .pdp .pef .pem .pff .pfm .pfx .pgm .php .php3 .php4 .php5 .phtml .pict .pl .pls .pm .png .pnm .pot .potm .potx .ppa .ppam .ppm .pps .ppsm .ppt .pptm .pptx .prn .ps .psb .psd .pst .ptx .pub .pwm .pxr .py .qt .r3d .raf .rar .raw .rdf .rgbe .rle .rqy .rss .rtf .rw2 .rwl .safe .sct .sdpx .shtm .shtml .slk .sln .sql .sr2 .srf .srw .ssi .st .stm .svg .svgz .swf .tab .tar .tbb .tbi .tbk .tdi .tga .thmx .tif .tiff .tld .torrent .tpl .txt .u3d .udl .uxdc .vb .vbs .vcs .vda .vdr .vdw .vdx .vrp .vsd .vss .vst .vsw .vsx .vtm .vtml .vtx .wb2 .wav .wbm .wbmp .wim .wmf .wml .wmv .wpd .wps .x3f .xl .xla .xlam .xlk .xlm .xls .xlsb .xlsm .xlsx .xlt .xltm .xltx .xlw .xml .xps .xsd .xsf .xsl .xslt .xsn .xtp .xtp2 .xyze .xz .zip -
Skipped files (not encrypted, probably):
info.hta info.txt boot.ini bootfont.bin ntldr ntdetect.com io.sys 1saas.exe
Executed Commands
Several commands gets executed in sub_4030E4 before encrypting the files using CreateProcessW:
- Delete all Volumes Shadow Copies (volumes backup or snapshot)
vssadmin delete shadows /all /quiet
wmic shadowcopy delete
-
Disable windows recovery mode
bcdedit /set {default} bootstatuspolicy ignoreallfailures bcdedit /set {default} recoveryenabled no -
Delete the backup catalog
wbadmin delete catalog -quiet -
Turn off the firewall and exit
netsh advfirewall set currentprofile state off netsh firewall set opmode mode=disable exit
The Encryption Process
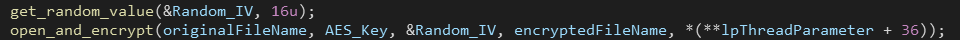
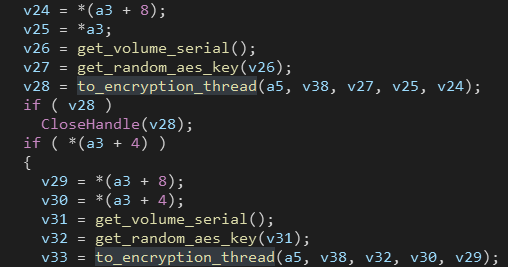
First the ransomware gets the logical drives then gets the volume serial number of the drive (32 bit value) and passes that value to the function get_random_aes_key which uses that serial number to create a unique AES key for that drive.
After that the key is passed to to_encryption_thread function which starts a new thread with the generated key as a ThreadParameter.
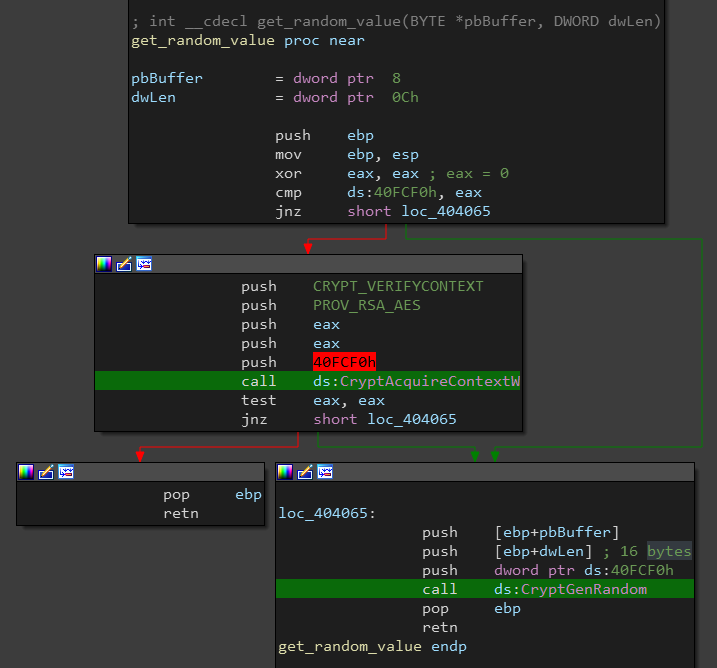
Although the key is the same for every file, the ransomware generates a random 16-bytes IV (initialization vector) for each file before encrypting it using CryptGenRandom.
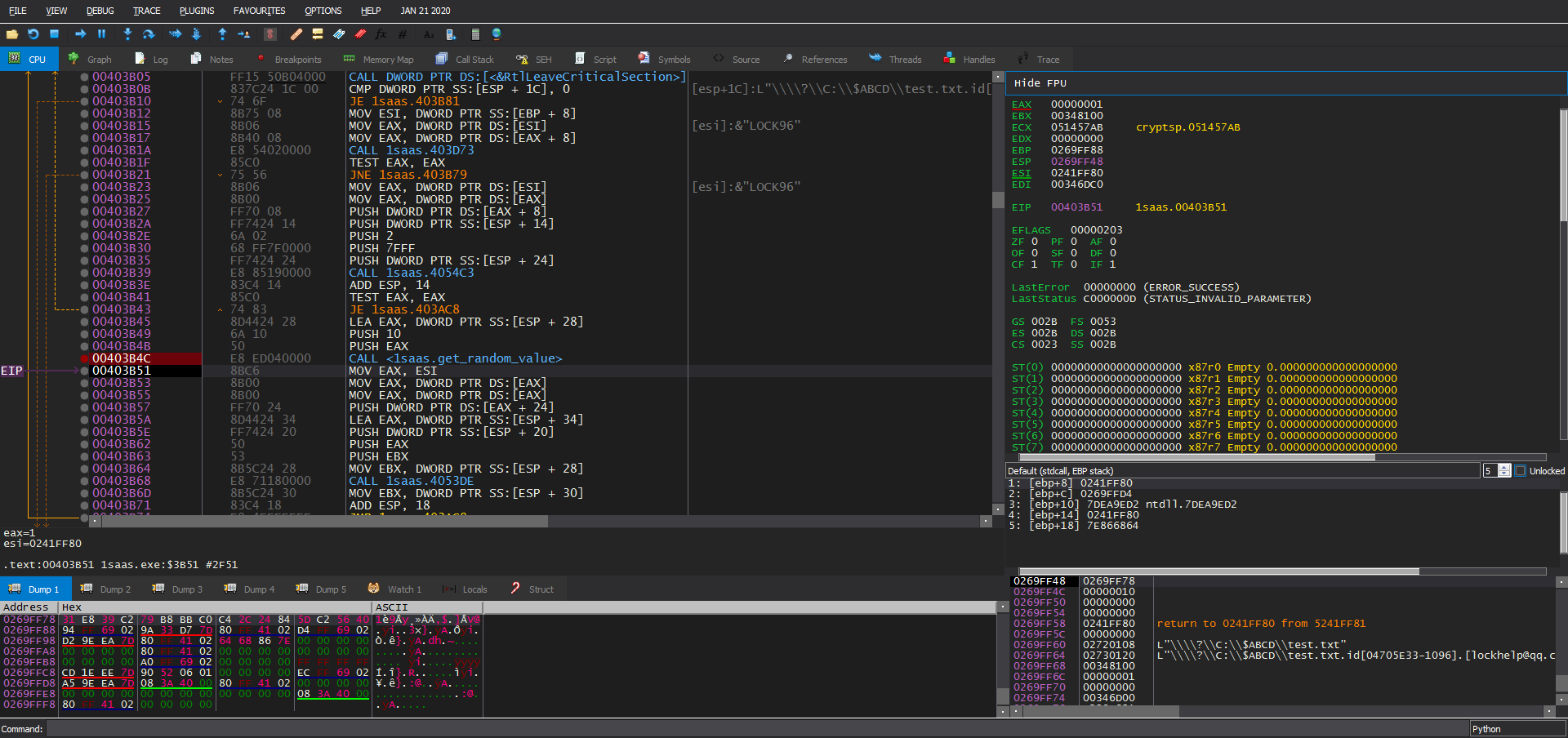
Here is a snapshot of get_random_value function:
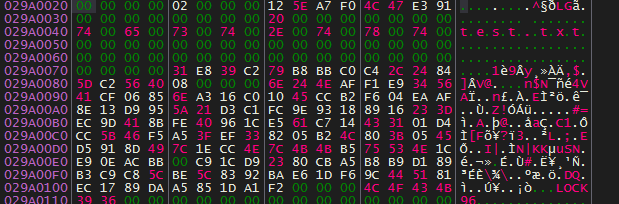
Let’s track the encryption process for a file called “test.txt” to see how it’s encrypted.
Using the debugger we can get the randomly generated IV for this file (31 E8 39 C2 79 B8 BB C0 C4 2C 24 84 5D C2 56 40).
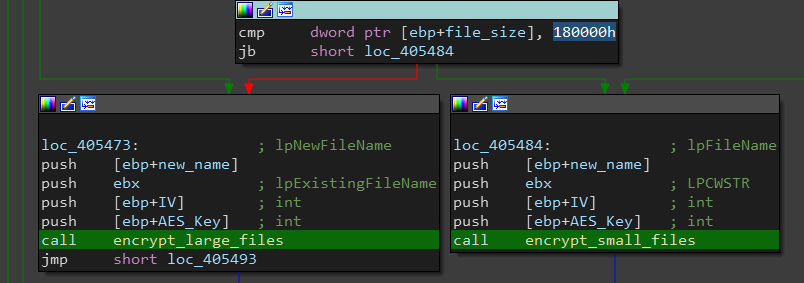
Next, open_and_encrypt function checks the file size, if it’s smaller than 0x180000 bytes it will go to encrypt_small_files else it will go to encrypt_large_files.
Encrypting Small Files
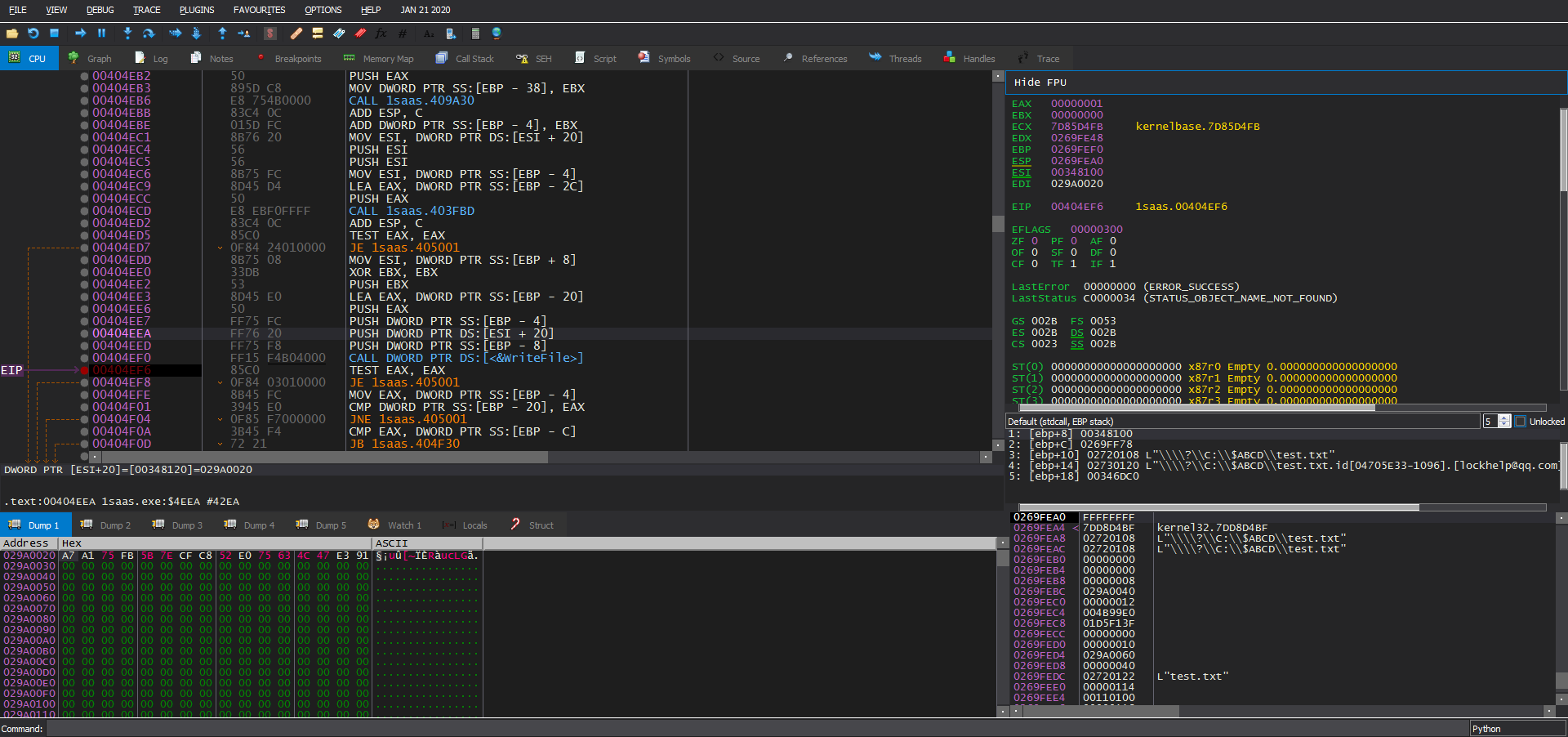
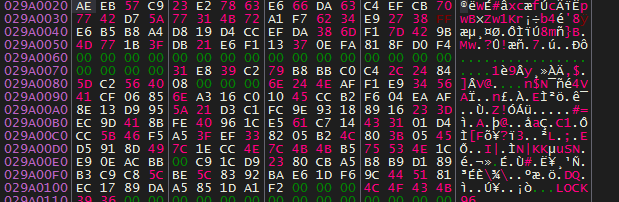
In the case of small files, The ransomware first creates a file with the new name (with the ransomware extension) then encrypts the file content and writes it to the newly created file.
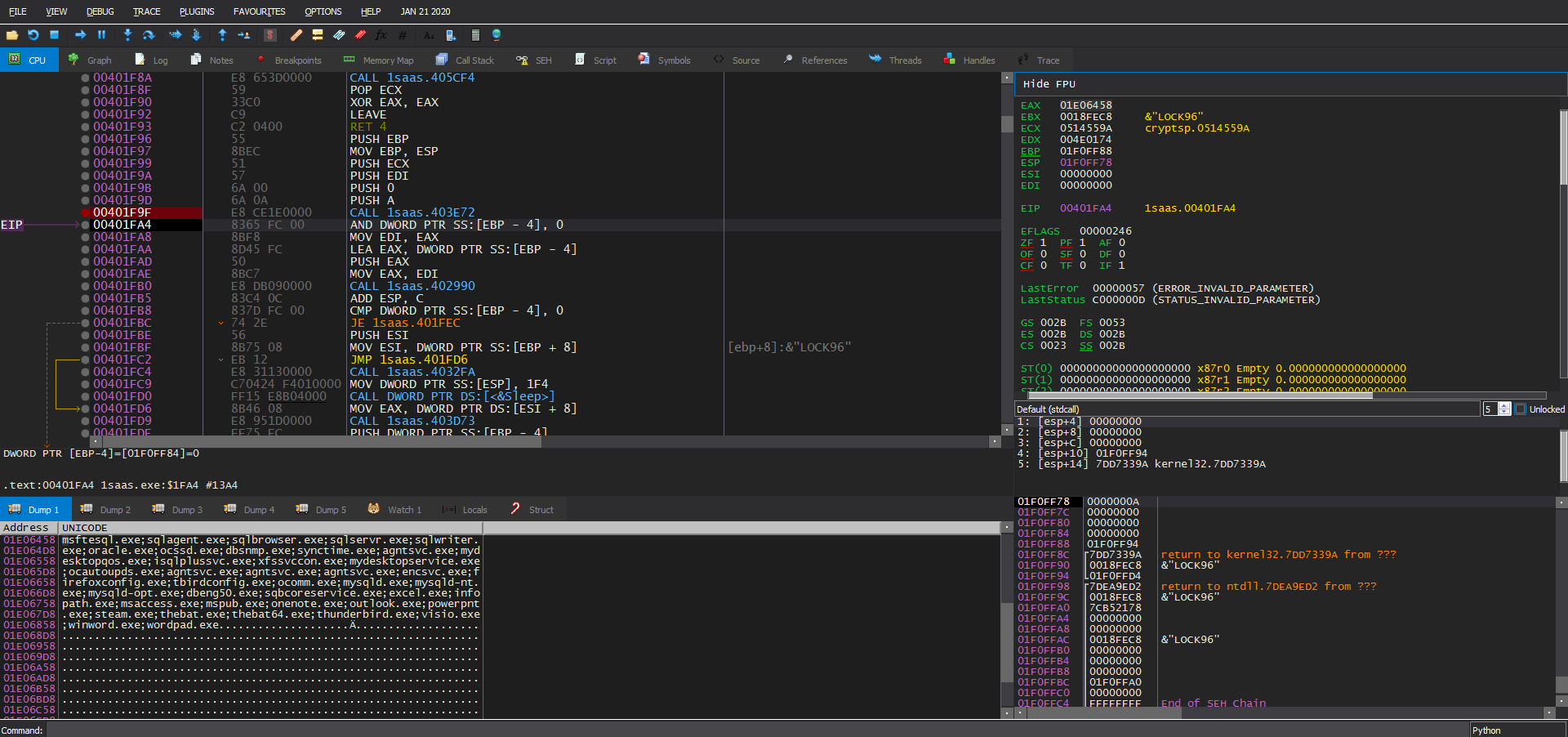
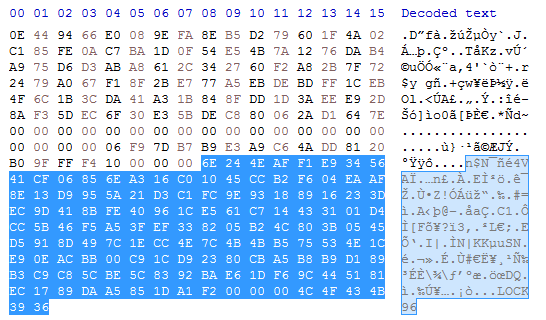
After that, the ransomware writes some metadata after the encrypted file content (possibly checksums + original file name + some padding nulls). Then it writes the random IV (you can see that it’s the same IV from above).
Finally it writes the encrypted AES key to end of the file followed by .LOCK96 and encrypts the metadata block (checksums + original file name).
 |
 |
After the encryption is done, the ransomware deletes the original file
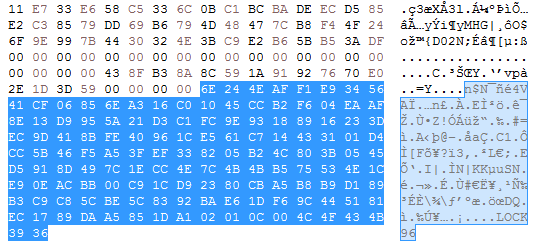
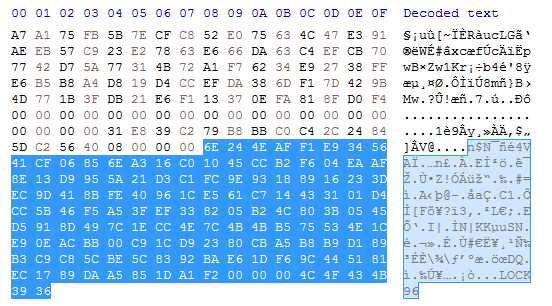
Here we can see two different small files after being encrypted and they have the same block at the end (encrypted AES key + “.LOCK96”):
 |
 |
Encrypting Large Files
Large files are encrypted differently, we can confirm that by creating a large file and filling it with \xFF. after the encryption we can see that some parts of the file are left unencrypted and some other parts are zerod out.
At the end of file file we can see the random IV + the same block similar to the small files (encrypted AES key + “.LOCK96”).
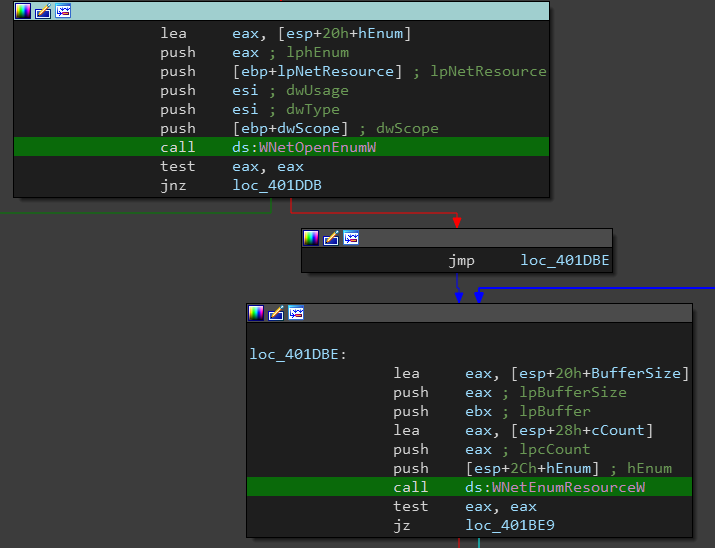
Encrypting Network Shares
The ransomware searches through network shared resources at sub_401B7D and starts new encryption threads for these resources.
That wraps up the analysis. This is my first time to fully analysis a ransomware from start to finish and it has been a great learning experience.
IOCs
Hashes
Phobos: a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2
Files
%ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup\1saas.exe
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\1saas.exe
Registry
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Emails
lockhelp@qq[.]com
External References
https://blog.malwarebytes.com/threat-analysis/2019/07/a-deep-dive-into-phobos-ransomware/