Pwnable.kr - flag
Challenge description:
Papa brought me a packed present! let’s open it.
This challenge is just a simple reverse engineering task, from the challenge description we can guess that the binary is packed.
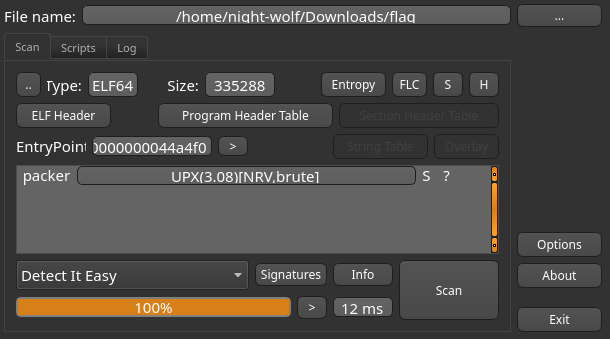
Using DIE (detect it easy), we can see that it’s packed using UPX.
we can unpack it easily using UPX:
$ upx -d flag
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2018
UPX 3.95 Markus Oberhumer, Laszlo Molnar & John Reiser Aug 26th 2018
File size Ratio Format Name
-------------------- ------ ----------- -----------
883745 <- 335288 37.94% linux/amd64 flag
Unpacked 1 file.
Now that the binary is unpacked, let’s jump to ida and do some reversing.
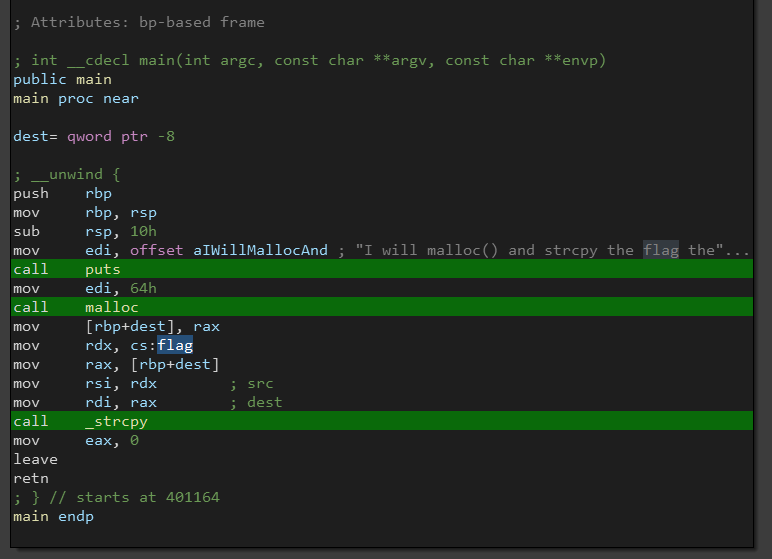
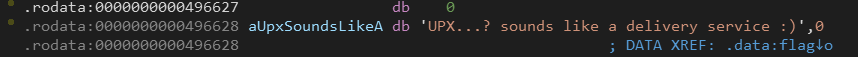
We can see that the main function is copying the flag into rdx, if we follow it to the .data section we will get the flag.
Solution:
Flag: UPX...? sounds like a delivery service :)